Mobile Security Framework (MobSF) is an open-source framework designed for mobile application security testing. It provides automated tools for static and dynamic analysis of Android and iOS applications.
MobSF is commonly used to analyse and assess mobile apps for security vulnerabilities, malware and privacy risks.
Installing MobSF
Installing MobSF on Ubuntu is pretty easy since there is a snap available. There are multiple versions available, which can be seen using the snap info command.
sudo snap info mobsf
name: mobsf
summary: Mobile Security Framework (MobSF)
publisher: Jitendra Patro (jitpatro)
store-url: https://snapcraft.io/mobsf
license: unset
description: |
**Mobile Security Framework (MobSF)** is an automated, all-in-one mobile application
(Android/iOS/Windows) pen-testing, malware analysis and security assessment framework capable of
performing static and dynamic analysis. MobSF supports mobile app binaries (APK, XAPK, IPA & APPX)
along with zipped source code and provides REST APIs for seamless integration with your CI/CD or
DevSecOps pipeline.The Dynamic Analyzer helps you to perform runtime security assessment and
interactive instrumented testing.
**Usage:-** https://github.com/JitPatro/Mobile-Security-Framework-MobSF-Snap
**Official Docs:-** https://mobsf.github.io/docs
**Installation:-** `sudo snap install mobsf`
commands:
- mobsf
snap-id: Zxwd96kEE6Wt0jNX6HUsp1aR6r5uY0RC
tracking: latest/stable
refresh-date: today at 10:21 GMT
channels:
latest/stable: v3.7.6-15-g4685d8e7 2023-11-16 (42) 504MB -
latest/candidate: v3.9.7-2-g99977da4 2024-07-14 (72) 457MB -
latest/beta: ↑
latest/edge: v4.3.0-2-gae34f7c0 2025-02-06 (84) 462MB -
Using the channel command, we can select the specific version we want. I found the edge version had issues logging in, but latest/stable worked without issues.
sudo snap install mobsf --channel latest/stable
For dynamic analysis, you will also need android-studio, so let’s install that at the same time.
sudo snap install android-studio
A docker image is available, but this would requires a lot of additional configuration to perform dynamic analysis. Similarly, you can clone the git repository and install from there, but that will require using a Python virtual environment.
We will be using MobSF to analyse an intentionally vulnerable application, InjuredAndroid that can be downloaded here: https://github.com/B3nac/InjuredAndroid.
Static Analysis
Use the mobsf command to start the application, then visit the web interface on http://127.0.0.1:8000. You can then upload a APK (Android) or IPA (Apple) file for static analysis.
Static analysis reviews the the source code to look for issues like insecure code, potential backdoors, hard coded credentials, and improper permissions. Uploading our InjuredAndroid.apk will take us to the following dashboard.
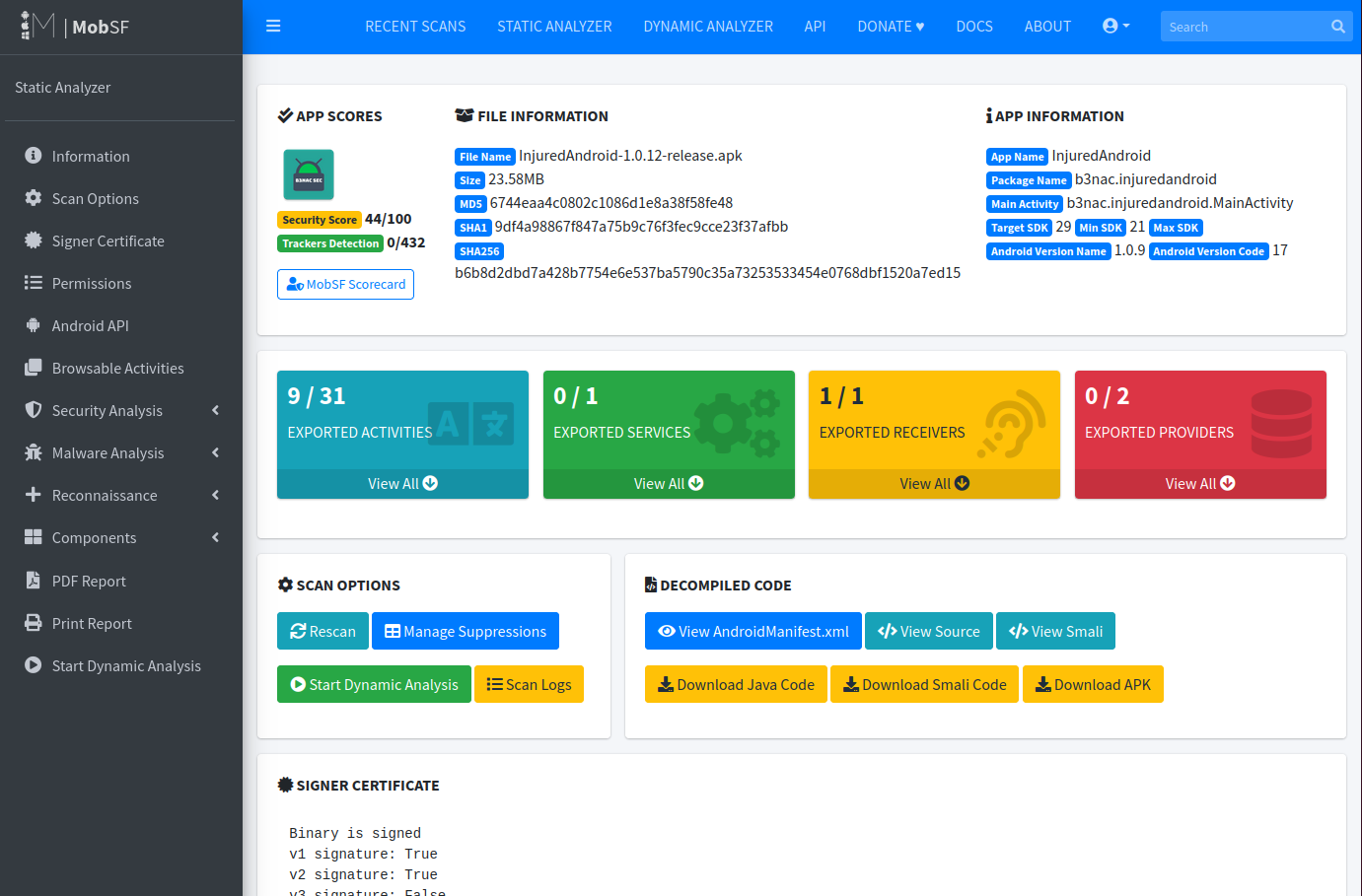
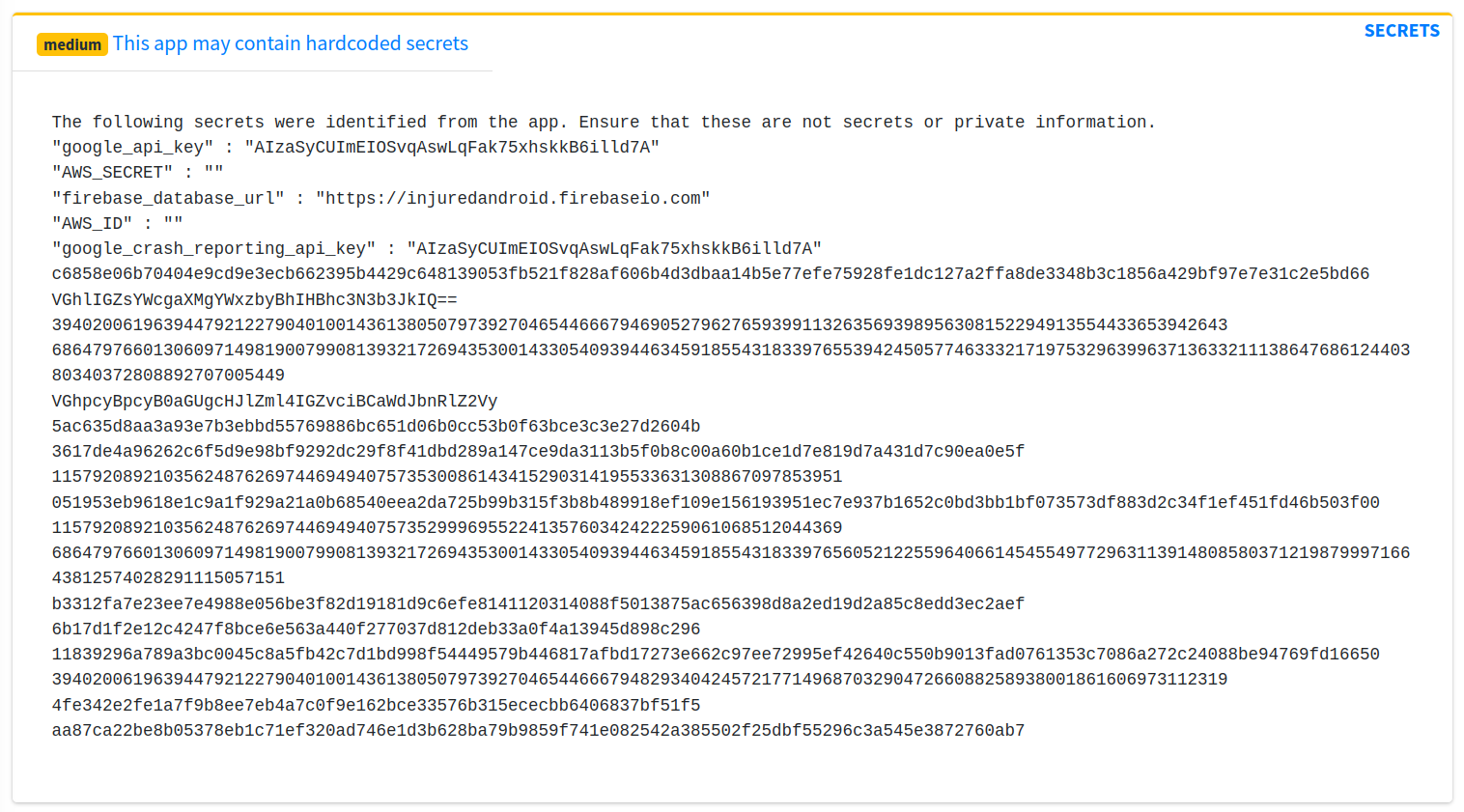
Clicking on the security score button will provide us with a list of potential issues. In the below output, we can see that it’s identified potentially hard coded credentials.
Dynamic Analysis
Dynamic analysis is performed when the application is ran in an emulated environment to observe its behaviour during execution. It can catch runtime issues and vulnerabilities such as unencrypted data transmission.
To configure this, use the Android Studio device manager to create a Nexus 6 Device, with API level 28. This is the latest API version MobSF supports.
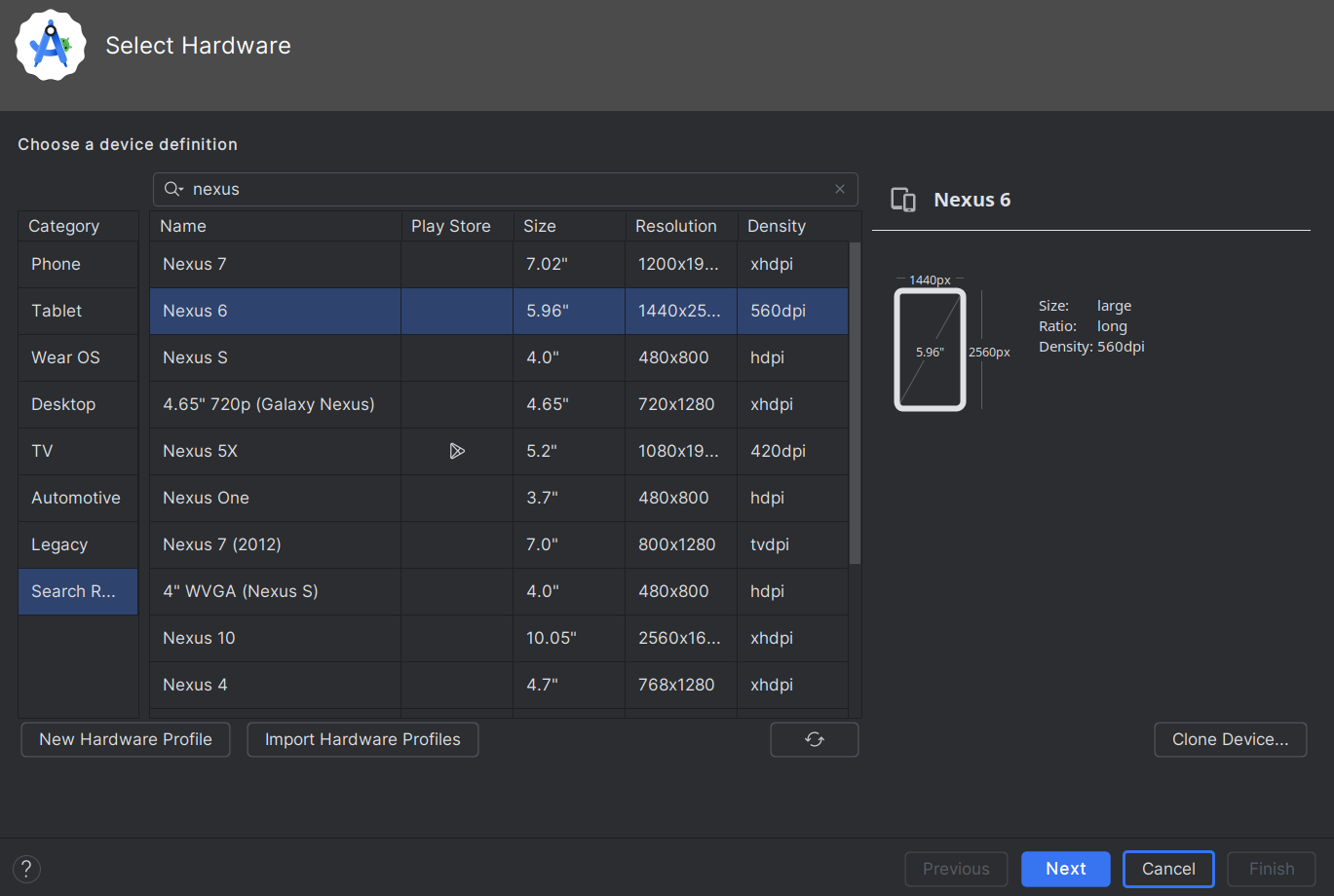
Next, use the emulator program that should be in your Android home directory to list the installed emulators.
/home/user/Android/Sdk/emulator/emulator -list-avds
Nexus_6_API_28
Nexus_6_API_35
Start our Nexus 6 emulator in the background by using the following command.
/home/user/Android/Sdk/emulator/emulator -avd Nexus_6_API_28 -writable-system -no-snapshot
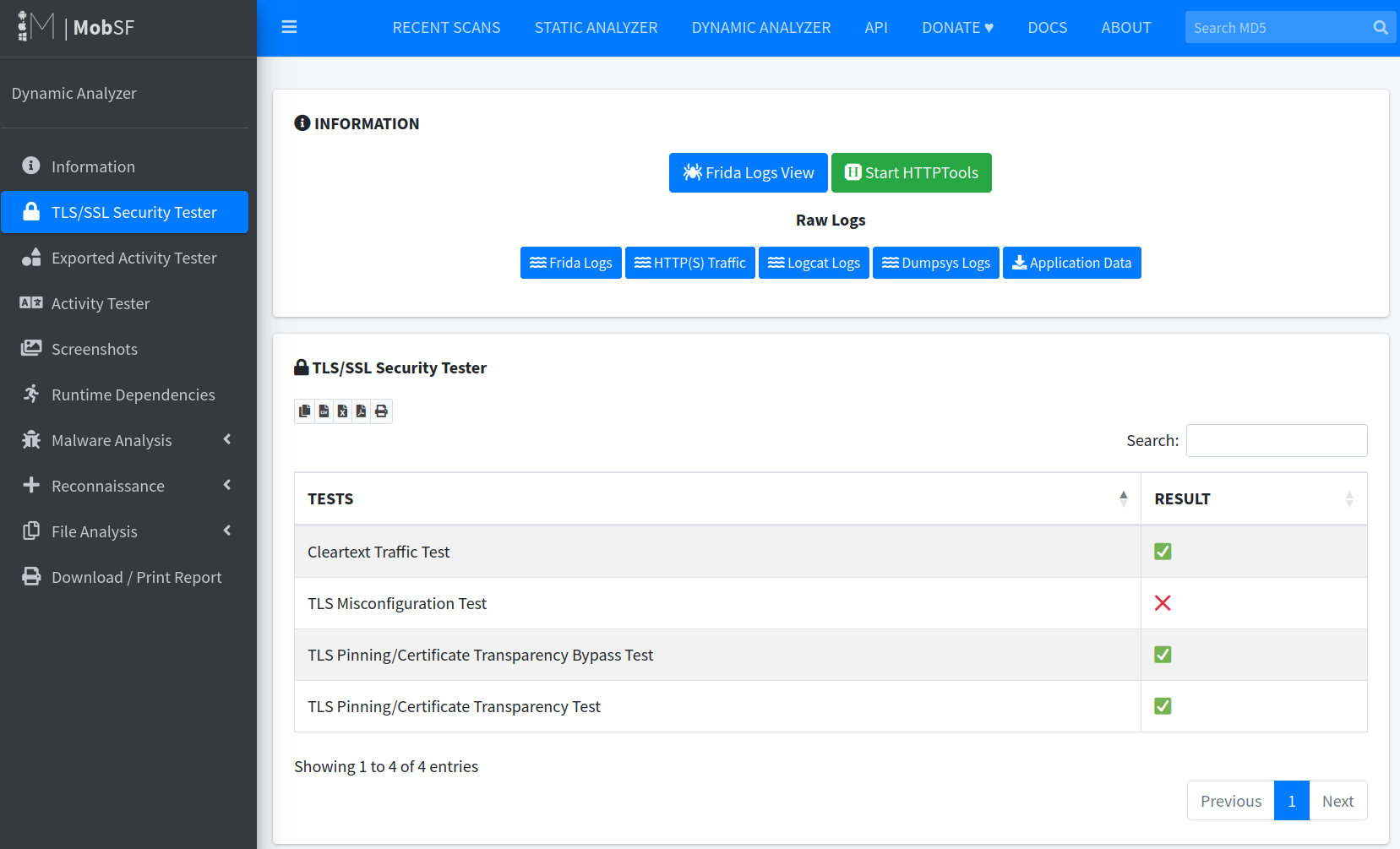
Now, after performing a static analysis in MobSF, select Dynamic Analyser > Dynamic Analysis. Run through the TLS/SSL Security tester, and activity tester options.
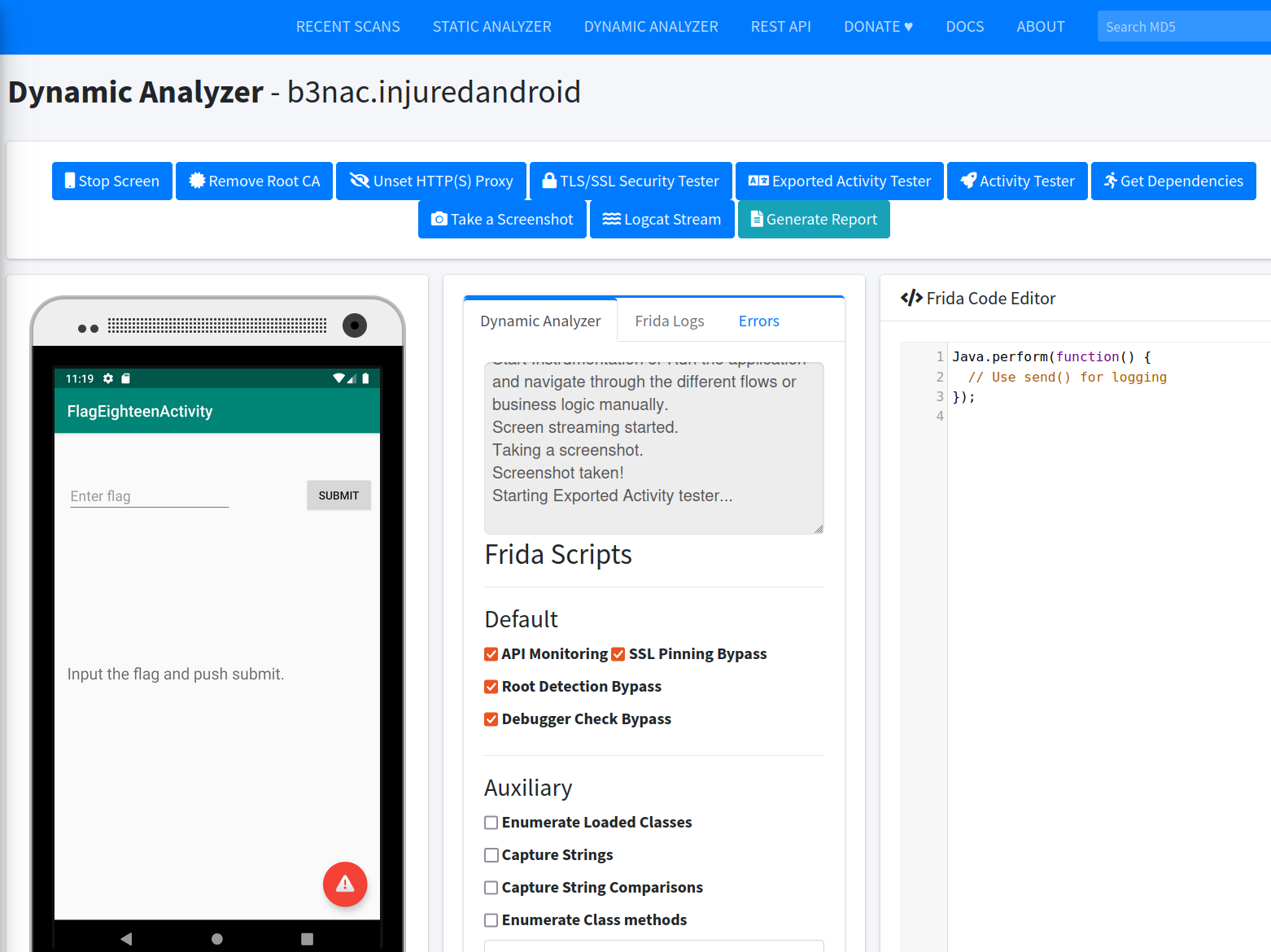
Once your done with the analysis options, select Generate Report. MobSF will create a report, detailing potential vulnerabilities such as:
- Insecure network communications (e.g., unencrypted data transmission)
- Sensitive data storage issues (e.g., storing credentials in plaintext)
- Application permissions (e.g., unnecessary permissions granted to the app)
These reports help you understand the security posture of the mobile application and identify areas for improvement.
In Conclusion
MobSF is an invaluable tool for performing mobile application security testing. It helps identify common vulnerabilities, such as hard coded credentials, insecure network communications, and improper permissions, in Android and iOS apps.