AD Explorer is an Active Directory Viewer and editor which is provided by Microsoft. The tool can be downloaded from Microsoft’s website here; https://learn.microsoft.com/en-us/sysinternals/downloads/adexplorer
AD Explorer has the ability to take snapshots of Active Directory configuration database to be analysed offline.
To analyse Active Directory attack paths, a Bloodhound ingester such as SharpHound is normally used. However, this is commonly detected by Anti-Virus Products. Based on the Bloodhound documentation, this is a known issue;
If you are on the red team side, you can employ some av-bypass strategies to avoid getting caught by AV. One of the best things you can do is stay completely off-disk when running SharpHound. Many command-and-control tools have in-memory .net assembly execution capabilities, such as Cobalt Strike’s execute-assembly and Covenant’s assembly commands. Using these commands will keep SharpHound totally off-disk when run on your target, which will go a very long way toward evading basic AV signatures.
Being a Microsoft signed executable, that is designed for AD administration rather than nefarious purposes AD Explorer is not commonly detected by Anti-Virus products.
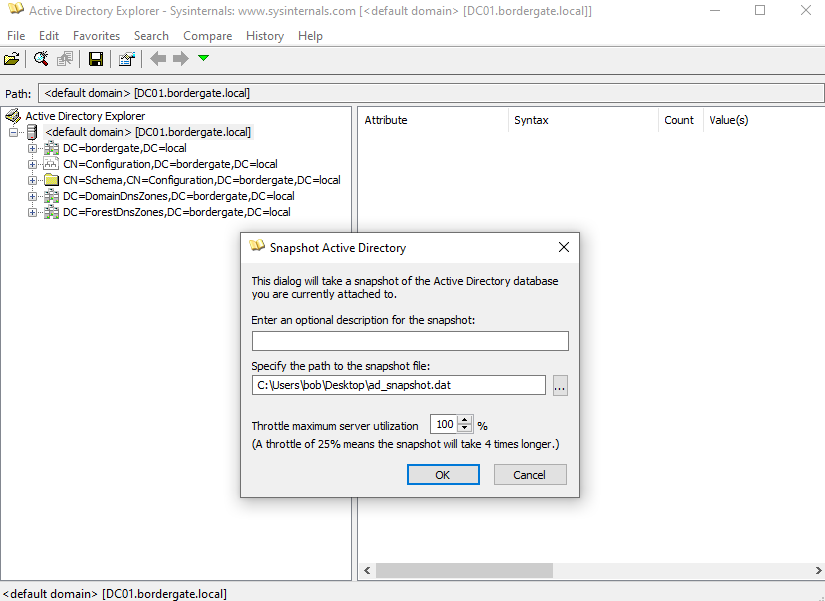
Taking a Snapshot with AD Explorer
To take a snapshot, just open the application and select File > Create Snapshot. There is unfortunately no progress bar to show how long it will take to complete. The snapshot will be stored in a .dat file.
ADExplorerSnapShot.py
This is a Python script that can convert AD Explorer snapshots to data that can be imported into Bloodhound. It can be downloaded here; https://github.com/c3c/ADExplorerSnapshot.py
Running the script with the snapshot file as it’s argument it should produce BloodHound compatible JSON files;
python3 ADExplorerSnapshot.py snapshot.dat -o /tmp/OUTPUT
[*] Server: CHDC01.cloudhopper.co.uk
[*] Time of snapshot: 2023-12-03T14:35:45
[*] Mapping offset: 0x2c0df4
[*] Object count: 3738
[+] Parsing properties: 1499
[+] Parsing classes: 269
[+] Parsing object offsets: 3738
[+] Restored pre-processed information from data cache
[+] Collecting data: 12 users, 53 groups, 7 computers, 33 certtemplates, 1 CAs, 0 trusts
[+] Output written to CHDC01.cloudhopper.co.uk_1701614145_*.json files
ls /tmp/OUTPUT
CHDC01.cloudhopper.co.uk_1701614145_cert_bh.json CHDC01.cloudhopper.co.uk_1701614145_domains.json
CHDC01.cloudhopper.co.uk_1701614145_cert_ly4k_cas.json CHDC01.cloudhopper.co.uk_1701614145_groups.json
CHDC01.cloudhopper.co.uk_1701614145_cert_ly4k_tpls.json CHDC01.cloudhopper.co.uk_1701614145_users.json
CHDC01.cloudhopper.co.uk_1701614145_computers.json
Adalanche
Adalanche is a tool similar to Bloodhound that can import AD Explorer snapshots. It can be downloaded from here; https://github.com/lkarlslund/Adalanche. We can import our AD Explorer snapshot, using the following command. The program will attempt to enumerate GPO information, which in this case is not reachable.
./adalanche collect activedirectory --adexplorerfile=./snapshot.dat
14:47:12.947 INFORMA Adalanche Open Source v2023.5.3 (commit aa4c038), (c) 2020-2022 Lars Karlslund, This program comes with ABSOLUTELY NO WARRANTY
14:47:12.948 INFORMA Collecting objects from AD Explorer snapshot ./snapshot.dat ...
14:47:12.948 INFORMA Loading raw AD Explorer snapshot into memory
14:47:12.972 INFORMA Reading header (takes a while) ...
14:47:13.290 INFORMA Collecting group policy files from \\cloudhopper.co.uk\sysvol\cloudhopper.co.uk\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9} ...
14:47:13.290 WARNING Can't access path, aborting this GPO ...
14:47:13.290 INFORMA Collecting group policy files from \\cloudhopper.co.uk\sysvol\cloudhopper.co.uk\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9} ...
14:47:13.290 WARNING Can't access path, aborting this GPO ...
14:47:13.290 INFORMA Terminating successfully
Next, run the tool in analyse mode to start viewing the results;
./adalanche analyze --datapath /home/kali/Tools/data
14:47:57.356 INFORMA Adalanche Open Source v2023.5.3 (commit aa4c038), (c) 2020-2022 Lars Karlslund, This program comes with ABSOLUTELY NO WARRANTY
14:47:57.357 INFORMA Scanning for data files from /home/kali/Tools/data ...
14:47:57.357 INFORMA Will process 1 files
14:47:57.428 INFORMA Loaded 1 files, skipped 0 files
14:47:57.609 INFORMA Loader Active Directory produced 3698 objects in 1 collections
14:47:57.609 INFORMA Loader Group Policy produced 0 objects in 0 collections
14:47:57.609 INFORMA Loader LocalMachine JSON file produced 1 objects in 1 collections
14:47:57.609 INFORMA We produced a total of 3699 objects from /home/kali/Tools/data
14:47:57.847 INFORMA Initiating merge with a total of 3729 objects
14:47:57.847 INFORMA Merging 3729 objects into the object metaverse
14:47:57.929 INFORMA After merge we have 3730 objects in the metaverse (merge eliminated -1 objects)
14:47:57.946 INFORMA We freed 0 objects
14:47:57.947 WARNING Detected 23 orphan objects in final results
14:47:57.947 INFORMA Time to UI done in 590.680663ms
14:47:57.947 INFORMA Listening - navigate to 127.0.0.1:8080 ... (ctrl-c or similar to quit)
14:47:57.948 WARNING Possible hardening? CN=Administrator,CN=Users,DC=cloudhopper,DC=co,DC=uk is a member of CN=Administrators,CN=Builtin,DC=cloudhopper,DC=co,DC=uk, which is not found - adding synthetic group. Your analysis will be degraded, try dumping with Domain Admin rights.
14:47:57.948 WARNING Possible hardening? CN=CHDC01,OU=Domain Controllers,DC=cloudhopper,DC=co,DC=uk is a member of CN=Pre-Windows 2000 Compatible Access,CN=Builtin,DC=cloudhopper,DC=co,DC=uk, which is not found - adding synthetic group. Your analysis will be degraded, try dumping with Domain Admin rights.
14:47:57.949 WARNING Possible hardening? CN=Guest,CN=Users,DC=cloudhopper,DC=co,DC=uk is a member of CN=Guests,CN=Builtin,DC=cloudhopper,DC=co,DC=uk, which is not found - adding synthetic group. Your analysis will be degraded, try dumping with Domain Admin rights.
14:47:57.957 WARNING Possible hardening? CN=Domain Users,CN=Users,DC=cloudhopper,DC=co,DC=uk is a member of CN=Users,CN=Builtin,DC=cloudhopper,DC=co,DC=uk, which is not found - adding synthetic group. Your analysis will be degraded, try dumping with Domain Admin rights.
14:47:57.963 INFORMA Time to analysis completed done in 606.424401ms
14:47:57.963 INFORMA Other: 1392, DomainDNS: 1, DNSNode: 14, DNSZone: 1, User: 12, Group: 80, ForeignSecurityPrincipal: 33, OrganizationalUnit: 2, BuiltinDomain: 1, Container: 300, Computer: 7, GroupPolicyContainer: 2, AttributeSchema: 1499, ClassSchema: 269, ControlAccessRight: 81, CertificateTemplate: 33, PKIEnrollmentService: 1, CertificationAuthority: 3, Machine: 7
14:48:05.352 INFORMA Graph query resulted in 9 nodes
Adalanche will load a web browser with a view similar view to Bloodhound;
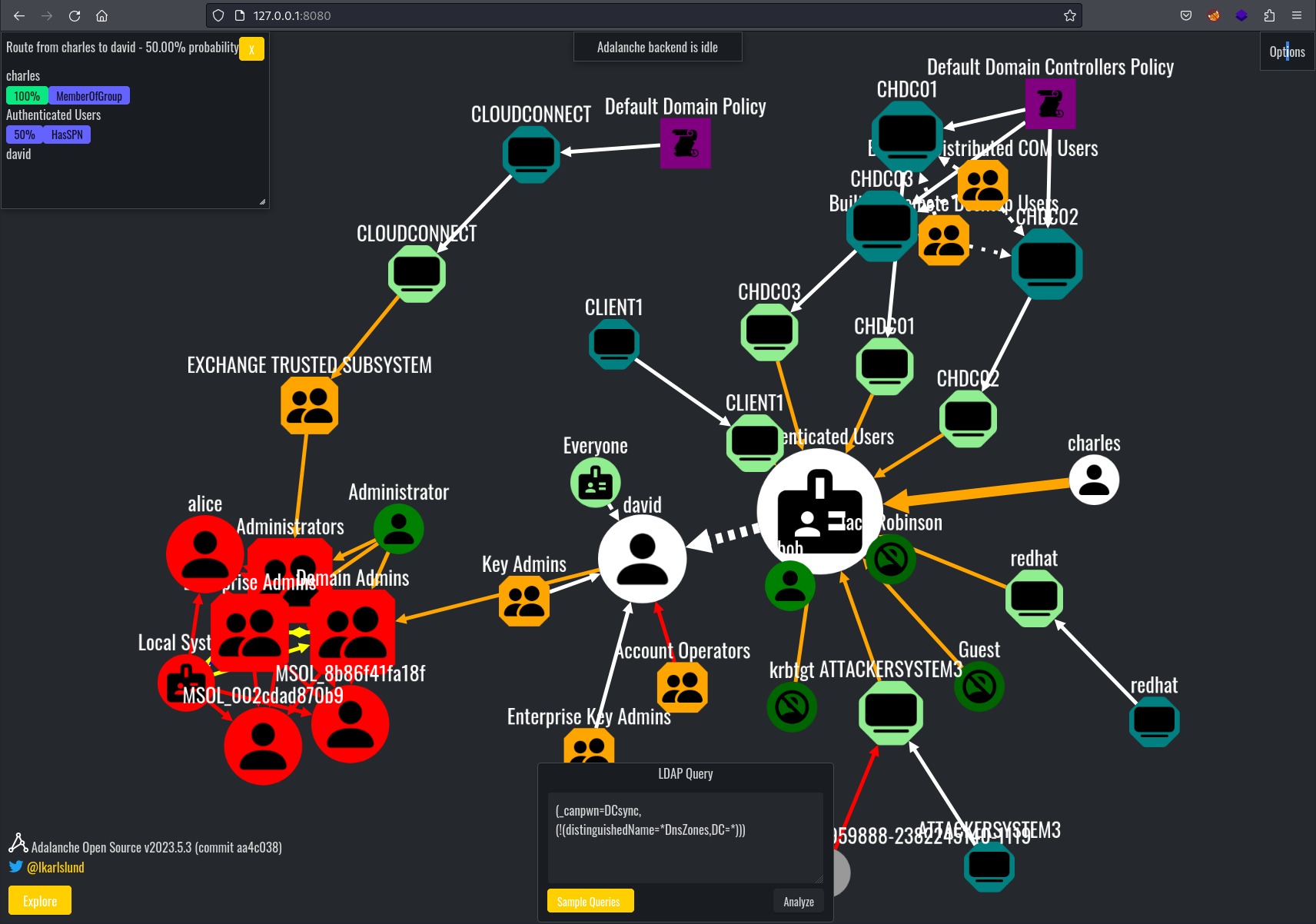
Right click on a node, and select “Set as route target”, then right click on a compromised node and select “Route to target”. A pop up window will appear in the top left showing potential attack paths. In this instance, the David account which is a domain admin has an SPN set, so could be Kerberoasted by Charles.
In Conclusion
It’s worth noting that AD Explorer will not collect some information that Sharphound normally collects, such as logged in user locations. I’ve had ADExplorerSnapShot.py fail to parse the output correctly for some domains, so having Adalanche as a backup is a good idea. Although Adalanche is currently not as fully featured as Bloodhound yet, it is in active development.