During a penetration test, password hashes are often captured using NTLM-SSP interception or by extracting the hashes directly from compromised systems. These passwords are often required to meet the default Active Directory password policy requirements.
Active Directory Password Policy
Most organisations use Active Directory for single sign on. As such, it’s important to tailor our password cracking attempts to meet the password requirements imposed by Active Directory.
As per Microsoft’s documentation by default passwords need to be at least 8 characters long, and contain characters from at least three of the following categories;
- Uppercase letters of European languages (A through Z, with diacritic marks, Greek and Cyrillic characters)
- Lowercase letters of European languages (a through z, sharp-s, with diacritic marks, Greek and Cyrillic characters)
- Base 10 digits (0 through 9)
- Non-alphanumeric characters (special characters): (~!@#$%^&*_-+=`|\(){}[]:;”‘<>,.?/) Currency symbols such as the Euro or British Pound aren’t counted as special characters for this policy setting.
- Any Unicode character that’s categorized as an alphabetic character but isn’t uppercase or lowercase. This group includes Unicode characters from Asian languages.
So, Password1 is a likely candidate 👍
Enumerating the Password Policy
To effectively crack passwords, you need to understand the password policy in place to adjust your approach to cracking accordingly. Crackmapexec can be used to determine the domain password policy:
crackmapexec smb 192.168.1.200 -u john -p 'Password1!' --pass-pol
SMB 192.168.1.200 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:bordergate.local) (signing:True) (SMBv1:False)
SMB 192.168.1.200 445 DC [+] bordergate.local\john:Password1!
SMB 192.168.1.200 445 DC [+] Dumping password info for domain: BORDERGATE
SMB 192.168.1.200 445 DC Minimum password length: 7
SMB 192.168.1.200 445 DC Password history length: 24
SMB 192.168.1.200 445 DC Maximum password age: 41 days 23 hours 53 minutes
SMB 192.168.1.200 445 DC
SMB 192.168.1.200 445 DC Password Complexity Flags: 000001
SMB 192.168.1.200 445 DC Domain Refuse Password Change: 0
SMB 192.168.1.200 445 DC Domain Password Store Cleartext: 0
SMB 192.168.1.200 445 DC Domain Password Lockout Admins: 0
SMB 192.168.1.200 445 DC Domain Password No Clear Change: 0
SMB 192.168.1.200 445 DC Domain Password No Anon Change: 0
SMB 192.168.1.200 445 DC Domain Password Complex: 1
SMB 192.168.1.200 445 DC
SMB 192.168.1.200 445 DC Minimum password age: 1 day 4 minutes
SMB 192.168.1.200 445 DC Reset Account Lockout Counter: 30 minutes
SMB 192.168.1.200 445 DC Locked Account Duration: 30 minutes
SMB 192.168.1.200 445 DC Account Lockout Threshold: None
SMB 192.168.1.200 445 DC Forced Log off Time: Not Set
Hashcat

Hashcat is a password recovery tool which can utilise a computers GPU to significantly speed up the process of finding passwords from their relevant hashed values.
To demonstrate the performance increase in using a GPU, a Ryzen 3600 CPU has the following hash cracking rate:
sudo hashcat -b -m 5600 -D 1
hashcat (v6.2.5) starting in benchmark mode
dlerror: libMesaOpenCL.so.1: cannot open shared object file: No such file or directory
OpenCL API (OpenCL 2.0 pocl 1.8 Linux, None+Asserts, RELOC, LLVM 11.1.0, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=====================================================================================================================================
* Device #1: pthread-AMD Ryzen 5 3600 6-Core Processor, 14957/29978 MB (4096 MB allocatable), 12MCU
OpenCL API (OpenCL 2.1 AMD-APP (3423.0)) - Platform #2 [Advanced Micro Devices, Inc.]
=====================================================================================
* Device #2: AMD Radeon RX 5700 XT 50th Anniversary, skipped
Benchmark relevant options:
===========================
* --opencl-device-types=1
* --optimized-kernel-enable
----------------------------
* Hash-Mode 5600 (NetNTLMv2)
----------------------------
Speed.#1.........: 74055.4 kH/s (82.65ms) @ Accel:512 Loops:1024 Thr:1 Vec:8
On the same system, utilising the 5700 XT GPU leads to a significantly faster cracking time:
sudo hashcat -b -m 5600
hashcat (v6.2.5) starting in benchmark mode
dlerror: libMesaOpenCL.so.1: cannot open shared object file: No such file or directory
OpenCL API (OpenCL 2.0 pocl 1.8 Linux, None+Asserts, RELOC, LLVM 11.1.0, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=====================================================================================================================================
* Device #1: pthread-AMD Ryzen 5 3600 6-Core Processor, skipped
OpenCL API (OpenCL 2.1 AMD-APP (3423.0)) - Platform #2 [Advanced Micro Devices, Inc.]
=====================================================================================
* Device #2: AMD Radeon RX 5700 XT 50th Anniversary, 8064/8176 MB (6949 MB allocatable), 20MCU
Benchmark relevant options:
===========================
* --optimized-kernel-enable
----------------------------
* Hash-Mode 5600 (NetNTLMv2)
----------------------------
Speed.#2.........: 1529.5 MH/s (54.61ms) @ Accel:2048 Loops:64 Thr:32 Vec:1
CPU Attempts per second: 74055400 (kH/s is 1,000 hashes per second)
GPU Attempts per second: 1529500000 (MH/s is 1,000,000 hashes per second)
So, roughly a 1965.35% performance increase 🙂
The reason for this performance increase is the GPU contains 2,560 RDNA cores, versus the Ryzen’s 6 processing cores. The GPU operating frequency may be lower (1905 Mhz for boost speed), than the Ryzen’s 4.6 GHz boost speed but the benefits of massively parallel operations wins out.
Configuring Hashcat on Ubuntu 22.04
The hashcat -I command can be used to see what processing units are available:
hashcat -I
hashcat (v6.2.5) starting in backend information mode
OpenCL Info:
============
OpenCL Platform ID #1
Vendor..: The pocl project
Name....: Portable Computing Language
Version.: OpenCL 2.0 pocl 1.8 Linux, None+Asserts, RELOC, LLVM 11.1.0, SLEEF, DISTRO, POCL_DEBUG
Backend Device ID #1
Type...........: CPU
Vendor.ID......: 1
Vendor.........: AuthenticAMD
Name...........: pthread-AMD Ryzen 5 3600 6-Core Processor
Version........: OpenCL 1.2 pocl HSTR: pthread-x86_64-pc-linux-gnu-znver2
Processor(s)...: 12
Clock..........: 4208
Memory.Total...: 29978 MB (limited to 4096 MB allocatable in one block)
Memory.Free....: 14957 MB
OpenCL.Version.: OpenCL C 1.2 pocl
Driver.Version.: 1.8
From the output, we can see only the CPU is detected. We need to install the OpenCL package for hashcat to detect our GPU. For AMD graphics cards, download the latest driver from AMD’s website and install with:
sudo dpkg -i amdgpu-install_22.10.2.50102-1_all.deb
sudo amdgpu-install --usecase=opencl --no-dkms
Hashcat should now be able to take advantage of the GPU:
sudo hashcat -I
hashcat (v6.2.5) starting in backend information mode
dlerror: libMesaOpenCL.so.1: cannot open shared object file: No such file or directory
OpenCL Info:
============
OpenCL Platform ID #1
Vendor..: The pocl project
Name....: Portable Computing Language
Version.: OpenCL 2.0 pocl 1.8 Linux, None+Asserts, RELOC, LLVM 11.1.0, SLEEF, DISTRO, POCL_DEBUG
Backend Device ID #1
Type...........: CPU
Vendor.ID......: 1
Vendor.........: AuthenticAMD
Name...........: pthread-AMD Ryzen 5 3600 6-Core Processor
Version........: OpenCL 1.2 pocl HSTR: pthread-x86_64-pc-linux-gnu-znver2
Processor(s)...: 12
Clock..........: 4208
Memory.Total...: 29978 MB (limited to 4096 MB allocatable in one block)
Memory.Free....: 14957 MB
OpenCL.Version.: OpenCL C 1.2 pocl
Driver.Version.: 1.8
OpenCL Platform ID #2
Vendor..: Advanced Micro Devices, Inc.
Name....: AMD Accelerated Parallel Processing
Version.: OpenCL 2.1 AMD-APP (3423.0)
Backend Device ID #2
Type...........: GPU
Vendor.ID......: 1
Vendor.........: Advanced Micro Devices, Inc.
Name...........: AMD Radeon RX 5700 XT 50th Anniversary
Version........: OpenCL 2.0
Processor(s)...: 20
Clock..........: 2100
Memory.Total...: 8176 MB (limited to 6949 MB allocatable in one block)
Memory.Free....: 8064 MB
OpenCL.Version.: OpenCL C 2.0
Driver.Version.: 3423.0 (HSA1.1,LC)
PCI.Addr.BDF...: 2b:00.0
Configuring Hashcat on Fedora 38
In Fedora 38, the following packages need to be installed;
sudo dnf install rocm-opencl rocminfo rocm-clinfo rocm-device-libs
Cracking Process
In general, the following steps seem effective at identifying easily guessed hashes;
- Run a large word list against the hashes. 100GB of word lists can be processed in around 38 minutes.
- Use rules with a base wordlist. For instance, looking for any dictionary words with modifications to change the first letter to a capital, and add numbers and letters to the end.
- If the password still isn’t cracked, resort to using mask attacks.
Windows Hashcat Formats
The full list of hashcat formats is available here. Below is a list of common Windows formats.
| Hash Format | Hash Type | Notes |
| NetNTLMv2 | 5600 | Responder Hashes |
| NTLM | 1000 | SAM/NTDS Hashes |
| Domain Cached Credentials 2 (DCC2) | 2100 | Cached passwords of previous logins |
| Kerberos 5, TGS-REP | 13100 | For Kerberoastable Accounts |
| Kerberos 5, AS-REP | 18200 | For ASRepRoastable Accounts |
Wordlist Attacks
Wordlists are useful for weeding out commonly used passwords. Hashcat can launch word list attacks using the following parameters:
hashcat -a 0 -m 5600 DumpNTLMv2.txt /PasswordLists/crackstation.txt
Below is a list of available wordlists that can be used for this purpose.
| Name | Size | Download | Notes |
| Crackstation | 15 GB | https://crackstation.net/ | Combination of wordlists, including non english words |
| Rocktastic | 13 GB | https://labs.nettitude.com/blog/rocktastic/ | Nettitude’s permutations of the infamous rockyou wordlist |
| RockYou2021 | 100 GB | https://github.com/ohmybahgosh/RockYou2021.txt | The largest collection of compromised passwords, including 8.4 billion entries |
| SecLists | 807Mb | https://github.com/danielmiessler/SecLists/tree/master/Passwords | Includes a large number of default passwords |
| Weakpass 2P | 9.4 Gb | https://weakpass.com/download | A password list complaint with the default windows password policy |
| English Words | 4.1Mb | https://github.com/dwyl/english-words | For use with rule attacks |
Custom word lists can also be created by scraping company websites using tools such as cewl.
Rule Attacks
Rule attacks take a base wordlist and modify it. This is useful since dictionary words with additional letters of special characters are common. Rule syntax is similar to John the Ripper. For instance, the following rule file will capitalize the first letter of each word and append a number to the end;
c
$1
$2
$3
$4
$5
$6
$7
$8
$9
hashcat -a 0 -m 5600 DumpNTLMv2.txt -r /usr/share/hashcat/rules/d3ad0ne.rule customwordlist.txt -d 2 -O
A comprehensive list of rule operators can be found on the hashcat website. NotSoSecure have released a third party ruleset OneRuleToRuleThemAll, which has also proved effective.
Mask Attacks
Mask Attacks check for passwords which match a specific pattern. Mask tokens are prefixed with a question mark character, and designate the character set to brute force;
- ?l = abcdefghijklmnopqrstuvwxyz
- ?u = ABCDEFGHIJKLMNOPQRSTUVWXYZ
- ?d = 0123456789
- ?h = 0123456789abcdef
- ?H = 0123456789ABCDEF
- ?s = «space»!”#$%&'()*+,-./:;<=>?@[\]^_`{|}~
- ?a = ?l?u?d?s
- ?b = 0x00 – 0xff
So, a mask for Password1! would be;
| Character | Mask Value |
| P | ?u |
| a | ?l |
| s | ?l |
| s | ?l |
| w | ?l |
| o | ?l |
| r | ?l |
| d | ?l |
| 1 | ?n |
| ! | ?s |
These patterns can be stored in a hcmask file. For instance, the contents of a default mask file looks like this:
head /usr/share/hashcat/masks/8char-1l-1u-1d-1s-compliant.hcmask
?d?d?d?d?d?l?u?s
?d?d?d?d?d?l?s?u
?d?d?d?d?d?u?l?s
?d?d?d?d?d?u?s?l
?d?d?d?d?d?s?l?u
?d?d?d?d?d?s?u?l
?d?d?d?d?l?d?u?s
?d?d?d?d?l?d?s?u
?d?d?d?d?l?l?u?s
?d?d?d?d?l?l?s?u
A mask attack can be launched with the following parameters:
hashcat -a 6 -m 5600 DumpNTLMv2.txt /usr/share/hashcat/masks/8char-1l-1u-1d-1s-compliant.hcmask -d 2 -O
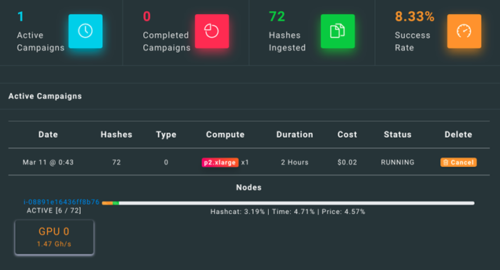
Cloud Cracking
Cracking passwords using a local computer is effective for discovering weak passwords, but for more complex passwords more computing power is likely needed. Coalfire have released a password cracking system for Amazon Web Services, called NPK. This system provides an easy to use web interface to launch password cracking campaigns with hashcat. Limits can be set on campaigns to ensure the AWS bill stays within reasonable levels.