Software restriction policies can be configured to prevent unknown executables from running on a system. This is an effective method of preventing malware execution.
Using the feature requires Windows 10 Professional or Enterprise. AppLocker and DeviceGuard offer more sophisticated functionality, but are only available in Windows Enterprise editions.
Configuration
Open gpedit.msc as an administrator. Navigate to Windows Settings > Security Settings > Software Restriction Policies. Click enforcement, and set the options below:
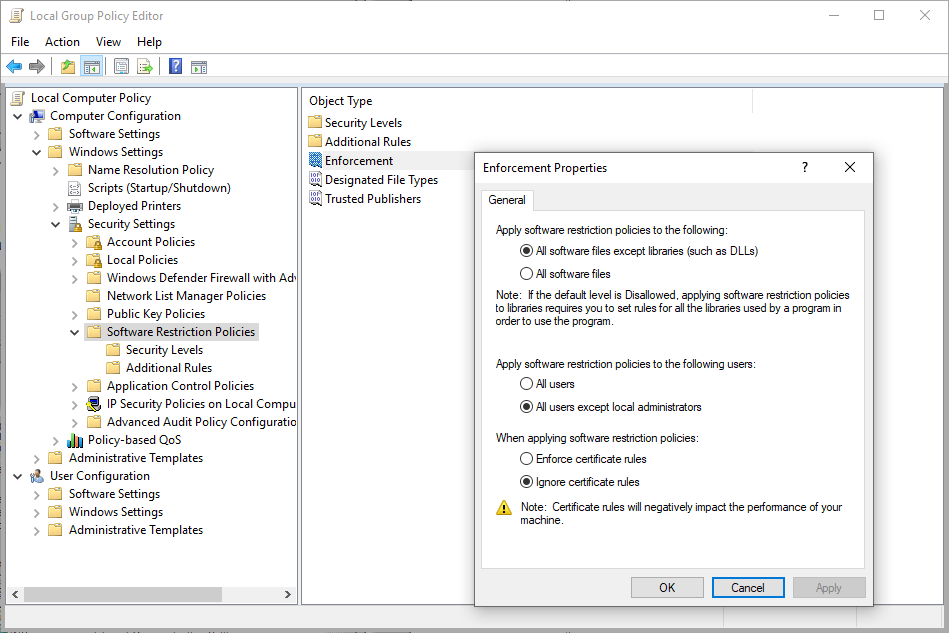
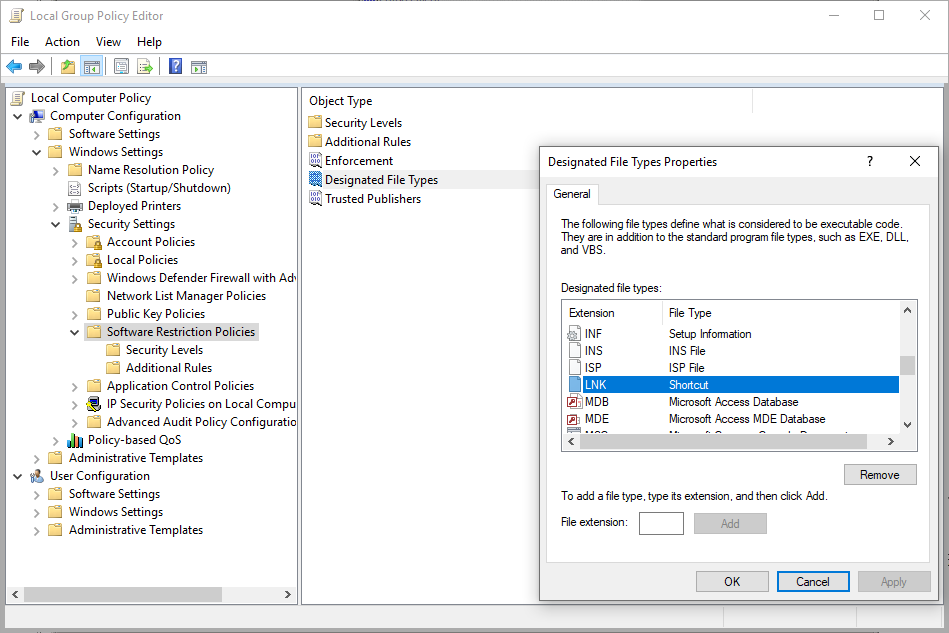
Click on designated filetypes and remove .LNK files. If you don’t do this, you will find shortcuts to programs no longer work…
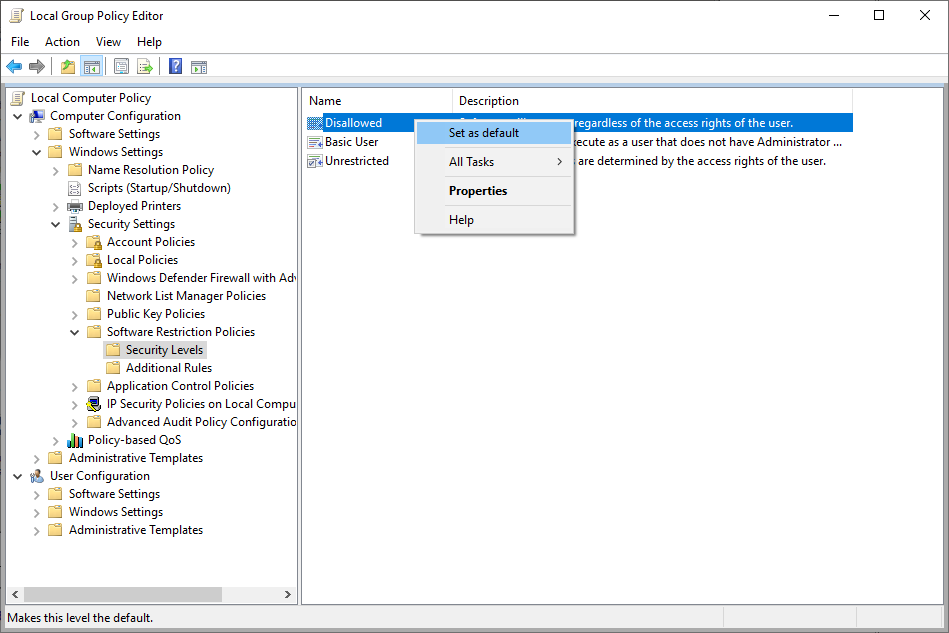
Under security levels, select “Disallowed” and select “Set as default”.
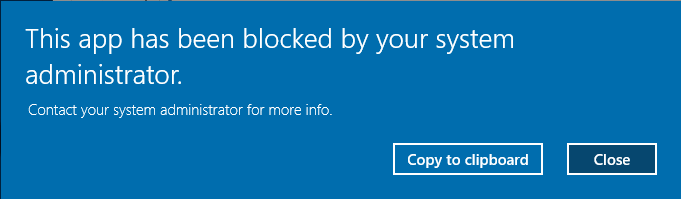
Now, if a user attempts to execute an application which has not been whitelisted they will receive the following error:
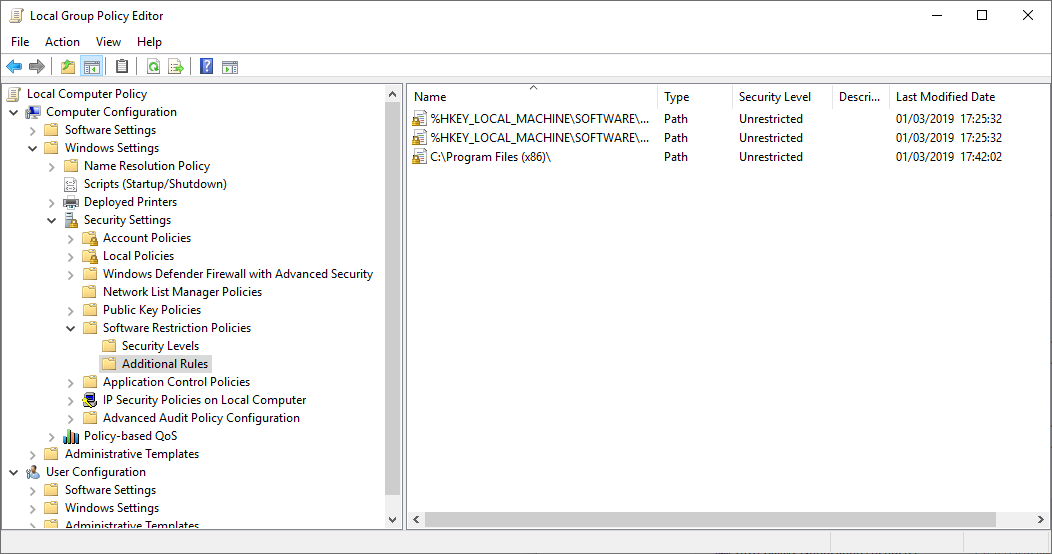
If you find an installed application is getting blocked, you can configure exceptions based on file hash, file path, or file signature. These can be configured under the additional rule section. For instance in the below example, I’ve added an entry for “C:\Program Files (x86)\”:
In Conclusion
Be aware that attackers with access to a system will be able to determine whitelisted locations. Care should be taken to ensure that user accounts do not have write access to whitelisted directories.